Event Reconstruction
Presenter Notes
What
String Encodings
Strings in memory
Command and Console history
Presenter Notes
String Encodings
Presenter Notes
Strings
ASCII v. Unicode
Windows API
- A = ASCII
- W = Unicode (wide)
Presenter Notes
ASCII
255 code positions
single byte
0 -> 127 = normal characters
128 -> 255 = special characters
Strings -a
- for ascii-only
Presenter Notes
Unicode
1,114,112 code positions
2 bytes
Allows other languages other than English
Searched with "wide" options
Strings -u
- for ascii-only
Presenter Notes
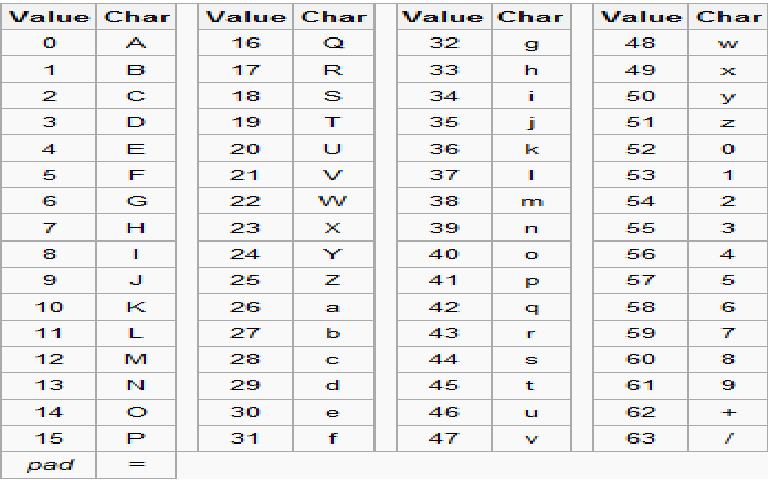
Base64
Presenter Notes
Base64
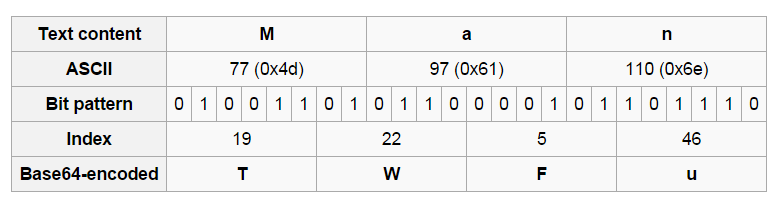
Binary data in an ASCII string with radix-64 representation.
ASCII String -> Each 6 bits creates index -> index into base64 for encoded character
Pads with '=' to indicate padding
[root&windows]#echo "Man" | base64
TWFuCg==
[root&windows]#echo "TWFuCg==" | base64 -d
Man
[root&windows]#echo "woman" | base64
d29tYW4K
Presenter Notes
Presenter Notes
Presenter Notes
In Memory
Presenter Notes
Extracting Strings
Volatility does not extract strings for you
- Python too slow
Volatility requires tool to output strings in form of
<decimal_offset>:<string>
<decimal_offset> <string>
Get ASCII and Unicode strings
Presenter Notes
How
Get strings from a raw physical memory sample
- if you want to map them back to virtual, that is.
- Can use "imagecopy" to make a crash dump/hibernation file into a raw dump!
Windows
Sysinternals strings does both ASCII and Unicode by default
strings.exe –q –o memory.dmp > strings.txt
Linux
GNU strings requires ASCII and Unicode separately
$ strings -td -a memory.dmp > strings.txt
$ strings -td -el -a memory.dmp >> strings.txt
Presenter Notes
Now
We have a text file of strings with the offset of where that string is in the memory dump
[root&windows]#wc -l strings.txt
6284806 strings.txt
[root&windows]#cat strings.txt
[snip]
88064077 !This program cannot be run in DOS mode.
88064215 ?Rich1
88064308 CS P
88064504 .pexe
[snip]
88850456 AuthzInitializeContextFromToken
88850488 AuthzInitializeObjectAccessAuditEvent2
88850528 AuthzAccessCheck
88850552 AuthzFreeAuditEvent
88850576 AuthzFreeContext
88850600 AuthzInitializeResourceManager
88850632 AuthzFreeResourceManager
88850760 RegCloseKey
88850840 __SuperClass = '
88853408 string too long
88853424 invalid string position
88853448 Invalid parameter passed to C runtime function.
Presenter Notes
Volatility
With a strings file, volatility can translate them to a virtual address if a mapping exists between the physical offset and virtual offset.
Strings
Match physical offsets to virtual addresses (may take a while, VERY verbose)
-s STRING_FILE, --string-file=STRING_FILE
File output in strings format (offset:string)
-S, --scan Use PSScan if no offset is provided
-o OFFSET, --offset=OFFSET
EPROCESS offset (in hex) in the physical address space
-p PID, --pid=PID Operate on these Process IDs (comma-separated)
Presenter Notes
Volatility Strings
[root&windows]#volatility -f lab5.vmem --profile Win7SP1x64 strings -s strings.txt > translated.txt
Presenter Notes

Presenter Notes
Translated.txt
[root&windows]#head -n 50 translated.txt
1631 [kernel:f88000a0565f kernel:ffffffd0e65f] t&fh
1775 [kernel:f88000a056ef kernel:ffffffd0e6ef] TCPAu2
[snip]
4273468 [FREE MEMORY] L$@H3
4273481 [FREE MEMORY] \$hH
4273486 [FREE MEMORY] t$pH
[snip]
4293475 [1244:03483363] cag\\V
4293546 [1244:034833aa] )46NPTl/3K%)A8?Sjq
4293565 [1244:034833bd] (/>IOV$*1&.;09M@Hf2;aMW
[snip]
Shows PID that owned the string and at what virtual address.
See what region of memory an address is in for a specific process/dll/kernel module...
Presenter Notes
Noise

Presenter Notes
Eliminate
ftrings with
- a certain length
- a certain extension
- an IP
Presenter Notes
Grep
[root&windows]#grep "\.pf" translated.txt | grep -i .exe
15508352 [kernel:f8a002c83380] \Device\HarddiskVolume1\Windows\Prefetch\SVCHOST.EXE-18D06B2E.pf
32931346 [kernel:f8a002a3ee12] WMIPRVSE.EXE-43972D0F.pfWMIPRVSE.EXE-43972D0F.PF
33072096 [kernel:f8a002d323e0] \Device\HarddiskVolume1\Windows\Prefetch\SVCHOST.EXE-135A30D8.pf
1031395400 [kernel:fa8001b9d848] \Device\HarddiskVolume1\Windows\Prefetch\VSSVC.EXE-04D079CC.pf
1031395552 [kernel:fa8001b9d8e0] \Device\HarddiskVolume1\Windows\Prefetch\W32TM.EXE-5D2265F4.pf
1031395704 [kernel:fa8001b9d978] \Device\HarddiskVolume1\Windows\Prefetch\WERFAULT.EXE-0897AE09.pf
1031395864 [kernel:fa8001b9da18] \Device\HarddiskVolume1\Windows\Prefetch\WERMGR.EXE-2A1BCBC7.pf
1031396016 [kernel:fa8001b9dab0] \Device\HarddiskVolume1\Windows\Prefetch\WMIADAP.EXE-369DF1CD.pf
1031396176 [kernel:fa8001b9db50] \Device\HarddiskVolume1\Windows\Prefetch\WMIPRVSE.EXE-43972D0F.pf
1033059648 [kernel:fa8001933d40] \Device\HarddiskVolume1\Windows\Prefetch\IPCONFIG.EXE-62724FE6.pf
1033067264 [kernel:fa8001935b00] \Device\HarddiskVolume1\Windows\Prefetch\SLUI.EXE-A65918C4.pf
1033072632 [kernel:fa8001936ff8] \Device\HarddiskVolume1\Windows\Prefetch\PING.EXE-B29F6629.pf
1033307768 [kernel:fa8001970678] \Device\HarddiskVolume1\Windows\Prefetch\MSCORSVW.EXE-FAA88858.pf
1033325216 [kernel:fa8001974aa0] \Device\HarddiskVolume1\Windows\Prefetch\MSCORSVW.EXE-98F0699A.pf
1033330800 [kernel:fa8001976070] \Device\HarddiskVolume1\Windows\Prefetch\SVCHOST.EXE-135A30D8.pf
1033336752 [kernel:fa80019777b0] \Device\HarddiskVolume1\Windows\Prefetch\SVCHOST.EXE-18D06B2E.pf
Presenter Notes
Grep
[root&windows]#grep "iexplorer" translated.txt
714446624 [2844:028f5720] %temp%\iexplorer.exe
715546636 [2844:02b7600c] ifexist%temp%\iexplorers.dllgotocon
715546722 [2844:02b76062] 0%temp%\iexplorer.exe
973140368 [2844:026ec190] hyiexplorerbarclass
973140388 [2844:026ec1a4] hyiexplorerbarclass
947465176 [2844:02a0abd8] c:\windows\fonts\iexplorer.exe
Presenter Notes
Free memory
Strings can be in freed or unallocated pages
31059195 [FREE MEMORY] Washington1
31059216 [FREE MEMORY] Redmond1
31059234 [FREE MEMORY] Microsoft Corporation1#0!
31059266 [FREE MEMORY] Microsoft Code Signing PCA0
Presenter Notes
Shared Pages
DLLs are shared
Files can be shared
Named shared memory
Stings shows strings of shared things with addr [thing1:addr thing2:addr ...]
[root&windows]#grep -E '[[0-9]+:[0-9]+ [0-9]+' translated.txt
96149592 [1244:74212058 1352:74212058] cname.comodoca.com
146513920 [372:00de2000 372:f900c0602000 424:f900c0602000 528:f900c0602000 536:f900c0602000 544:f900c0602000 644:f900c0602000 720:f900c0602000 812:f900c0602000 856:f900c0602000 884:f900c0602000 972:f900c0602000 248:f900c0602000 300:f900c0602000 1064:00782000 1064:f900c0602000 1104:f900c0602000 1252:f900c0602000 1560:f900c0602000 1608:f900c0602000 1864:f900c0602000 2012:f900c0602000 1552:f900c0602000 2164:f900c0602000 2812:f900c0602000 2924:f900c0602000 2640:f900c0602000 2844:f900c0602000 1928:f900c0602000 2272:f900c0602000 920:f900c0602000 2396:f900c0602000] F9B-9EF4-7114B42285A9}
131777536 [2448:73347400 1244:73347400 1352:73347400] OLEACC.dll
131777552 [2448:73347410 1244:73347410 1352:73347410] OLEAUT32.dll
131777600 [2448:73347440 1244:73347440 1352:73347440] WINMM.dll
131777616 [2448:73347450 1244:73347450 1352:73347450] WindowsCodecs.dll
Presenter Notes
Shared things
131777616 [2448:73347450 1244:73347450 1352:73347450] WindowsCodecs.dll
[root&windows]#volatility -f lab5.vmem --profile Win7SP1x64 pslist -p 2448,1244,1352
Volatility Foundation Volatility Framework 2.4
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0xfffffa8000dd0630 iexplore.exe 2448 2508 22 684 1 1 2015-05-20 16:10:09 UTC+0000
0xfffffa8000f263a0 iexplore.exe 1244 2448 46 886 1 1 2015-05-20 16:10:11 UTC+0000
0xfffffa8001105b30 iexplore.exe 1352 2448 37 925 1 1 2015-05-20 16:11:00 UTC+0000
[root&windows]#volatility -f lab5.vmem --profile Win7SP1x64 dlllist -p 2448,1244,1352
Volatility Foundation Volatility Framework 2.4
************************************************************************
iexplore.exe pid: 2448
Command line : "C:\Program Files (x86)\Internet Explorer\iexplore.exe"
Note: use ldrmodules for listing DLLs in Wow64 processes
Presenter Notes
Looking for 2448:73347450
[root&windows]#volatility -f lab5.vmem --profile Win7SP1x64 ldrmodules -p 2448
Volatility Foundation Volatility Framework 2.4
Pid Process Base InLoad InInit InMem MappedPath
-------- -------------------- ------------------ ------ ------ ----- ----------
2448 iexplore.exe 0x0000000073200000 False False False \Windows\winsxs\x86_microsoft.windows.common-controls_6595b64144ccf1df_6.0.7601.17514_none_41e6975e2bd6f2b2\comctl32.dll
Presenter Notes
Dump DLL and view Strings
[root&windows]#mkdir comctl32
/bin/mkdir: created directory `comctl32'
[root&windows]#volatility -f lab5.vmem --profile Win7SP1x64 dlldump -p 2448 -b 0x0000000073200000 -D comctl32/
Volatility Foundation Volatility Framework 2.4
Process(V) Name Module Base Module Name Result
------------------ -------------------- ------------------ -------------------- ------
0xfffffa8000dd0630 iexplore.exe 0x0000000073200000 UNKNOWN OK: module.2448.3e5d0630.73200000.dll
[root&windows]#strings comctl32/module.2448.3e5d0630.73200000.dll | grep WindowsCodecs
WindowsCodecs.dll
Presenter Notes
WoW64
Windows On Windows
Interface between 32-bit NtDll.dll
Wow64.dll is interface between 32-bit applications and a 64-bit Kernel
Loads a x86 version of Ntdll.dll with all thunks (values) to Ntoskrnl.exe entry-point functions
Presenter Notes
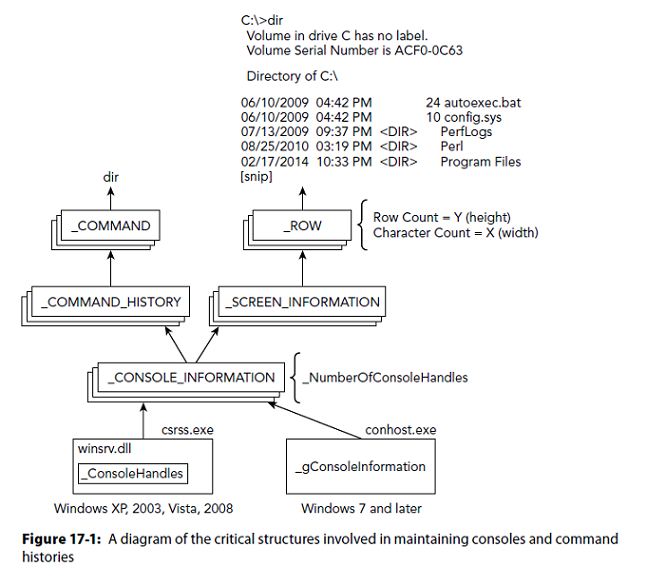
Command History
Presenter Notes
Cmd.exe
No command history on disk like UNIX bash shell
Windows < 7 used csrss.exe with SYSTEM privileges to broker commands
- Always running with machine powered on
- Contains history buffer and stdio, stdout, stderr
Windows > 7 uses conhost.exe (console host) and runs with same permissions as user
Cmd.exe is a client-server architecture
Presenter Notes
Conhost.exe
Undocumented functions
- SrvAllocCOnsole
- AllocateCommandHistory
- AddCommand
- FindCommandHistory
- RemoveCommand
- FindMachingCommand
- FindCommandHistory
Presenter Notes
Finding History
conhost.exe!_gConsoleInformation
Contains _COMMAND_HISTORY and _SCREEN_INFORMATION
Each history buffer has a _COMMAND for each command typed
Screen contains _ROW structs to show console windows height
Presenter Notes
conhost.exe!_gConsoleInformation
>>> dt("_CONSOLE_INFORMATION")
'_CONSOLE_INFORMATION' (None bytes)
0x18 : ProcessList ['_LIST_ENTRY'] #_CONSOLE_PROCESS
0x98 : CurrentScreenBuffer ['pointer', ['_SCREEN_INFORMATION']]
0x9c : ScreenBuffer ['pointer', ['_SCREEN_INFORMATION']]
0xd4 : HistoryList ['_LIST_ENTRY'] #_COMMAND_HISTORY
0xdc : ExeAliasList ['_LIST_ENTRY']
0xe4 : HistoryBufferCount ['unsigned short']
0xe6 : HistoryBufferMax ['unsigned short']
0xe8 : CommandHistorySize ['unsigned short']
0xec : OriginalTitle ['pointer', ['String', {'length': 256, 'encoding': 'utf16'}]]
0xf0 : Title ['pointer', ['String', {'length': 256, 'encoding': 'utf16'}]]
Presenter Notes
_COMMAND_HISTORY In Memory
>>> dt("_COMMAND_HISTORY")
'_COMMAND_HISTORY' (None bytes)
0x0 : ListEntry ['_LIST_ENTRY']
0x8 : Flags ['Flags', {'bitmap': {'Reset': 1, 'Allocated': 0}}]
0xc : Application ['pointer', ['String', {'length': 256, 'encoding': 'utf16'}]]
0x10 : CommandCount ['short']
0x12 : LastAdded ['short']
0x14 : LastDisplayed ['short']
0x16 : FirstCommand ['short']
0x18 : CommandCountMax ['short']
0x1c : ProcessHandle ['unsigned int']
0x20 : PopupList ['_LIST_ENTRY']
0x28 : CommandBucket ['array', <function <lambda> at 0xa0ed10c>, ['pointer', ['_COMMAND']]]
>>> dt("_COMMAND")
'_COMMAND' (None bytes)
0x0 : CmdLength ['unsigned short']
0x2 : Cmd ['String', {'length': <function <lambda> at 0xa0ed0d4>, 'encoding': 'utf16'}]
Presenter Notes
_SCREEN_INFORMATION in Memory
>>> dt("_SCREEN_INFORMATION")
'_SCREEN_INFORMATION' (None bytes)
0x8 : ScreenX ['short']
0xa : ScreenY ['short']
0x3c : Rows ['pointer', ['array', <function <lambda> at 0xa0ed1ec>, ['_ROW']]]
0xdc : Next ['pointer', ['_SCREEN_INFORMATION']]
#Content within screen buffer
>>> dt("_ROW")
'_ROW' (28 bytes)
0x8 : Chars ['pointer', ['String', {'length': 256, 'encoding': 'utf16'}]]
Presenter Notes
Graphical
Presenter Notes
Console Settings?
HKEY_CURRENT_USER\Console
- HistoryBufferSize
- NumberOfHistoryBuffers
Changed from cmd.exe itself... screen buffer, window size, font, etc...
Volatility allows configurable settings to be altered
- -h on plugins shows how to adjust size
- biffer size and command count
Presenter Notes
CmdScan
Extract command history by scanning for _COMMAND_HISTORY
Locate command history with default size (50)
Searches in pages owned by csrss or conhost
Validates _COMMAND_HISTORY
Traverse CommandBucket
Shows which broker is being used and which applications used it
Presenter Notes
CmdScan
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x64 cmdscan
Volatility Foundation Volatility Framework 2.4
**************************************************
CommandProcess: conhost.exe Pid: 2132
CommandHistory: 0x1de4c0 Application: TPAutoConnect.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x60
**************************************************
CommandProcess: conhost.exe Pid: 112
CommandHistory: 0x2cf9e0 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 9 LastAdded: 8 LastDisplayed: 8
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x68
Cmd #0 @ 0x2ce4b0: ipconfig
Cmd #1 @ 0x2ceee0: ping 4.2.2.2
Cmd #2 @ 0x2cef10: ping google.com
Cmd #3 @ 0x2ce4f0: cd ..
Cmd #4 @ 0x2ce1b0: dir
Cmd #5 @ 0x2ce510: cd ..
Cmd #6 @ 0x2ce250: dir
Cmd #7 @ 0x2ce530: cd bin
Cmd #8 @ 0x2cfc70: dir
Presenter Notes
Consoles
Scans for _CONSOLE_INFORMATION
Access to screen buffers
- stdout, stderr, stdin
Presenter Notes
Consoles
**************************************************
ConsoleProcess: csrss.exe Pid: 7888
Console: 0x4c2404 CommandHistorySize: 50
HistoryBufferCount: 4 HistoryBufferMax: 4
OriginalTitle: Command Prompt
Title: Command Prompt
AttachedProcess: cmd.exe Pid: 5544 Handle: 0x25c
----
CommandHistory: 0x4c2c30 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 12 LastAdded: 11 LastDisplayed: 11
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x25c
Cmd #0 at 0x4c1f90: d:
Cmd #1 at 0xf41280: cd inetlogs
Cmd #2 at 0xf412e8: cd w*46
Cmd #3 at 0xf41340: type <REDACTED>.log | find "<REDACTED>.jpg" | find "GET"
Cmd #4 at 0xf41b10: c:
Cmd #5 at 0xf412a0: cd\windows\system32\<REDACTED>\sample
Cmd #6 at 0xf41b20: ftp <REDACTED>.com
Cmd #7 at 0xf41948: notepad <REDACTED>.log
Cmd #8 at 0x4c2388: notepad <REDACTED>.log
Cmd #9 at 0xf43e70: ftp <REDACTED>.com
Cmd #10 at 0xf43fb0: dir
Cmd #11 at 0xf41550: notepad <REDACTED>.log
----
Screen 0x4c2b10 X:80 Y:3000
Dump:
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
C:\WINDOWS\system32\<REDACTED>\sample>dir
Volume in drive C has no label.
Volume Serial Number is AC20-A7D1
Directory of C:\WINDOWS\system32\<REDACTED>\sample
05/22/2012 09:18 PM <DIR> .
05/22/2012 09:18 PM <DIR> ..
02/28/2012 08:30 AM 0 <REDACTED>.att
02/28/2012 08:30 AM 341 <REDACTED>.bdy
02/28/2012 08:30 AM 474 <REDACTED>.epj
02/28/2012 08:30 AM 0 <REDACTED>.fad
02/28/2012 08:27 AM 100 <REDACTED>.txt
02/28/2012 08:30 AM 0 <REDACTED>.vad
08/03/2011 06:48 AM 323 <REDACTED>.vbs
02/28/2012 08:05 AM 501,760 <REDACTED>.hlp
05/22/2012 09:18 PM 44,184,520 <REDACTED>.log
05/22/2012 09:10 PM 24,686,680 <REDACTED>.log
05/22/2012 09:09 PM 3,272,096 <REDACTED>.log
05/21/2012 01:25 AM 28,672 JpgCommand.exe
08/03/2011 06:49 AM 4,608 <REDACTED>.exe
01/20/2012 09:07 AM 57,344 <REDACTED>.hlp
14 File(s) 72,736,918 bytes
2 Dir(s) 39,034,490,880 bytes free