Windows Internals
Presenter Notes
What
Windows Internals
-
SSDT
-
IDT
-
GDT
Rootkit Analysis
Presenter Notes
Trap
Interrupts and exceptions that divert the control flow of the operating system
Typically from User -> Kernel
Trap handlers are given control and they act on a particular interrupt to exception.
Presenter Notes
Interrupt v. Exception
Exceptions
- Execution of a particular instruction
- Memory-access, debugger instructions...
Interrupts
- I/O devices, clocks/timers
Hardware and Software can create both.
Presenter Notes
Interrupts
Device drivers set up Interrupt Service Routines (ISR) that get control on device interrupts
Software passes control to a specific system service function in the executive layer of the kernel from a trap handler.
>>> dt("_KINTERRUPT")
'_KINTERRUPT' (632 bytes)
0x0 : Type ['short']
0x2 : Size ['short']
0x4 : InterruptListEntry ['_LIST_ENTRY']
0xc : ServiceRoutine ['pointer', ['void']]
0x10 : MessageServiceRoutine ['pointer', ['void']]
0x14 : MessageIndex ['unsigned long']
0x18 : ServiceContext ['pointer', ['void']]
0x1c : SpinLock ['unsigned long']
0x20 : TickCount ['unsigned long']
0x24 : ActualLock ['pointer', ['unsigned long']]
0x28 : DispatchAddress ['pointer', ['void']]
0x2c : Vector ['unsigned long']
0x30 : Irql ['unsigned char']
0x31 : SynchronizeIrql ['unsigned char']
0x32 : FloatingSave ['unsigned char']
0x33 : Connected ['unsigned char']
0x34 : Number ['unsigned long']
0x38 : ShareVector ['unsigned char']
0x39 : Pad ['array', 3, ['unsigned char']]
0x3c : Mode ['Enumeration', {'target': 'long', 'choices': {0: 'LevelSensitive', 1: 'Latched'}}]
0x40 : Polarity ['Enumeration', {'target': 'long', 'choices': {0: 'InterruptPolarityUnknown', 1: 'InterruptActiveHigh', 2: 'InterruptActiveLow'}}]
0x44 : ServiceCount ['unsigned long']
0x48 : DispatchCount ['unsigned long']
0x50 : Rsvd1 ['unsigned long long']
0x58 : DispatchCode ['array', 135, ['unsigned long']]
Presenter Notes
Interrupt Dispatch Table (IDT)
At the time of a hardware interrupt, an Interrupt Request (IRQ) is queried
IRQ is then passed into the Interrupt Dispatch Table (IDT)
IDT passes control to the proper interrupt dispatch routine
At system boot, Windows fill the IDT with kernel routines for each interrupt and exception (up to 256).
Each processor has its own IDT
Presenter Notes
Volatility idt
Display Interrupt Descriptor Table
Displays IDT for each CPU
Shows CPU number, GDT selector, address and owning module.
IDT should be in the .text section!
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 idt
Volatility Foundation Volatility Framework 2.4
CPU Index Selector Value Module Section
------ ------ ---------- ---------- -------------------- ------------
0 0 0x8 0x82842690 ntoskrnl.exe .text
0 1 0x8 0x82842820 ntoskrnl.exe .text
0 2 0x58 0x00000000 UNKNOWN
0 3 0x8 0x82842c90 ntoskrnl.exe .text
0 4 0x8 0x82842e18 ntoskrnl.exe .text
0 5 0x8 0x82842f78 ntoskrnl.exe .text
0 6 0x8 0x828430ec ntoskrnl.exe .text
0 7 0x8 0x828436e8 ntoskrnl.exe .text
0 8 0x50 0x00000000 UNKNOWN
0 9 0x8 0x82843b48 ntoskrnl.exe .text
0 A 0x8 0x82843c6c ntoskrnl.exe .text
0 B 0x8 0x82843dac ntoskrnl.exe .text
0 C 0x8 0x8284400c ntoskrnl.exe .text
0 D 0x8 0x828442fc ntoskrnl.exe .text
[snip]
Presenter Notes
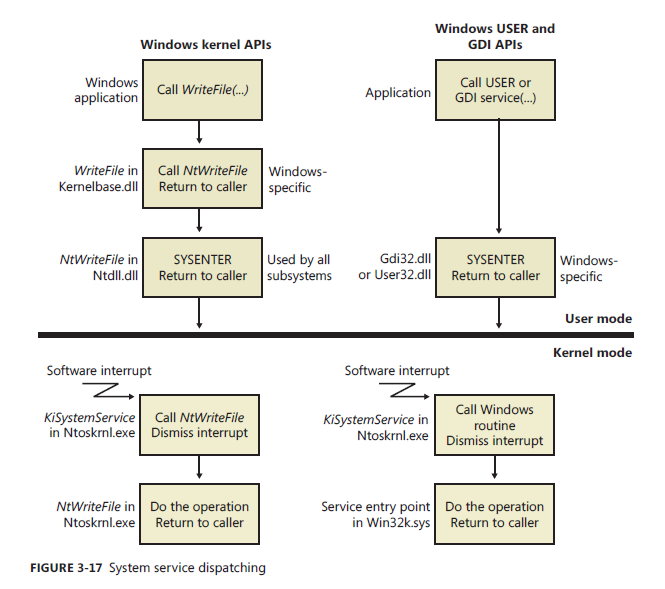
System Service Dispatching
Previous Mode is a flag set to determine if the thread was kernel or user mode.
Zw function calls are exported by the kernel
- Avaliable for drivers
- Doesn't set the previous mode flag
- Trampolines into the Nt system
Nt function calls
- Set the previous mode flag
System dispatcher, KiSystemService, creates kernel stacks and executes system services.
- Only copies information from user stack if previous mode is user mode
Presenter Notes
Descriptor Tables
KeServiceDescriptorTable
- core executive
- Ntdll.dll
KeServiceDescriptorTableShadow
- Windows Graphical Device Interface (GDI) and USER services
- Win32.sys
- user32.dll and gdi32.dll
Remember SSDT plugin from Rootkits!
Presenter Notes
Presenter Notes
Kernel Protection
Presenter Notes
Global Descriptor Table (GDT)
A callgate to perform kernel operations from ring 3!
A FAR CALL instruction is used by user mode to call into kernel mode.
Each processor can have a GDT.
Should be in protected memory
System memory segmentation
These are suspicious...
All IDT entries except task gates should point at GDT index 1
Presenter Notes
Volatility GDT
Print the GDT
Shows what selectors have a call gate and at what address
Disassemble in volshell the addresses!
Will show CallGate as the type!
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 gdt
Volatility Foundation Volatility Framework 2.4
CPU Sel Base Limit Type DPL Gr Pr
------ ---------- ---------- ---------- -------------- ------ ---- ----
0 0x0 0x00000000 0x00000000 <Reserved> 0 By Np
0 0x8 0x00000000 0xffffffff Code RE Ac 0 Pg P
0 0x10 0x00000000 0xffffffff Data RW Ac 0 Pg P
0 0x18 0x00000000 0xffffffff Code RE Ac 3 Pg P
0 0x20 0x00000000 0xffffffff Data RW Ac 3 Pg P
0 0x28 0x801db000 0x000020ab TSS32 Busy 0 By P
0 0x30 0x8292ec00 0x00003748 Data RW Ac 0 By P
Presenter Notes
Recap
GDT = Callgate to make Ring 3 perform Ring 0 operations
IDT = Table read to deliver interrupt vectors to handlers
SSDT = Table containing pointers for each system call handler