Registry
Presenter Notes
Windows Registry Review
Hierarchal database
Maintains configuration settings - Applications - Hardware - Devices - Users - Wireless networks
Presenter Notes
Physical Structure
Binary files
Stored in RAM and hard drive
Limited data types
Logical Structure
Contains Five Root Hives
Each Hive consists of Hives and Keys
Each key has a set of
triples - Subkey list
- Last access time
Presenter Notes
Root Hives
HKEY_USERS
- Contains all the actively loaded user profiles for the system
HKEY_CURRENT_USER
- Is the active, loaded user profile currently logged on
HKEY_LOCAL_MACHINE
- Contains configuration information for the system bot HW and SW
HKEY_CURRENT_CONFIG
- Contains the hardware profile the system uses at startup
HKEY_CLASSES_ROOT
- Contains configuration information for which apps open which files
Presenter Notes
Memory
The registry is constantly processed at run time
Lots of registry artifacts in RAM
Recently ran programs, password hashes, new keys and values
_CMHIVE data structure for disk
_HHIVE is the header for a specific hive
Presenter Notes
_CMHIVE
Pool tag is CM10
>>> dt("_CMHIVE")
'_CMHIVE' (1584 bytes)
0x0 : Hive ['_HHIVE']
0x2ec : FileHandles ['array', 6, ['pointer', ['void']]]
0x304 : NotifyList ['_LIST_ENTRY']
0x30c : HiveList ['_LIST_ENTRY']
0x314 : PreloadedHiveList ['_LIST_ENTRY']
0x31c : HiveRundown ['_EX_RUNDOWN_REF']
0x320 : ParseCacheEntries ['_LIST_ENTRY']
0x328 : KcbCacheTable ['pointer', ['_CM_KEY_HASH_TABLE_ENTRY']]
0x32c : KcbCacheTableSize ['unsigned long']
0x330 : Identity ['unsigned long']
0x334 : HiveLock ['pointer', ['_FAST_MUTEX']]
0x338 : ViewLock ['_EX_PUSH_LOCK']
0x33c : ViewLockOwner ['pointer', ['_KTHREAD']]
0x340 : ViewLockLast ['unsigned long']
0x344 : ViewUnLockLast ['unsigned long']
0x348 : WriterLock ['pointer', ['_FAST_MUTEX']]
0x34c : FlusherLock ['pointer', ['_ERESOURCE']]
0x350 : FlushDirtyVector ['_RTL_BITMAP']
0x358 : FlushOffsetArray ['pointer', ['CMP_OFFSET_ARRAY']]
0x35c : FlushOffsetArrayCount ['unsigned long']
0x360 : FlushHiveTruncated ['unsigned long']
0x364 : FlushLock2 ['pointer', ['_FAST_MUTEX']]
0x368 : SecurityLock ['_EX_PUSH_LOCK']
0x36c : MappedViewList ['_LIST_ENTRY']
0x374 : PinnedViewList ['_LIST_ENTRY']
0x37c : FlushedViewList ['_LIST_ENTRY']
0x384 : MappedViewCount ['unsigned short']
0x386 : PinnedViewCount ['unsigned short']
0x388 : UseCount ['unsigned long']
0x38c : ViewsPerHive ['unsigned long']
0x390 : FileObject ['pointer', ['_FILE_OBJECT']]
0x394 : LastShrinkHiveSize ['unsigned long']
0x398 : ActualFileSize ['_LARGE_INTEGER']
0x3a0 : FileFullPath ['_UNICODE_STRING']
0x3a8 : FileUserName ['_UNICODE_STRING']
0x3b0 : HiveRootPath ['_UNICODE_STRING']
0x3b8 : SecurityCount ['unsigned long']
0x3bc : SecurityCacheSize ['unsigned long']
0x3c0 : SecurityHitHint ['long']
0x3c4 : SecurityCache ['pointer', ['_CM_KEY_SECURITY_CACHE_ENTRY']]
0x3c8 : SecurityHash ['array', 64, ['_LIST_ENTRY']]
0x5c8 : UnloadEventCount ['unsigned long']
0x5cc : UnloadEventArray ['pointer', ['pointer', ['_KEVENT']]]
0x5d0 : RootKcb ['pointer', ['_CM_KEY_CONTROL_BLOCK']]
0x5d4 : Frozen ['unsigned char']
0x5d8 : UnloadWorkItem ['pointer', ['_CM_WORKITEM']]
0x5dc : UnloadWorkItemHolder ['_CM_WORKITEM']
0x5f0 : GrowOnlyMode ['unsigned char']
0x5f4 : GrowOffset ['unsigned long']
0x5f8 : KcbConvertListHead ['_LIST_ENTRY']
0x600 : KnodeConvertListHead ['_LIST_ENTRY']
0x608 : CellRemapArray ['pointer', ['_CM_CELL_REMAP_BLOCK']]
0x60c : Flags ['unsigned long']
0x610 : TrustClassEntry ['_LIST_ENTRY']
0x618 : FlushCount ['unsigned long']
0x61c : CmRm ['pointer', ['_CM_RM']]
0x620 : CmRmInitFailPoint ['unsigned long']
0x624 : CmRmInitFailStatus ['long']
0x628 : CreatorOwner ['pointer', ['_KTHREAD']]
0x62c : RundownThread ['pointer', ['_KTHREAD']]
Presenter Notes
We care about
0x0 HIVE
0x30c HiveList. Doble list of _CMHIVEs using _LIST_ENTRY
0x3a0 FullFilePath \Device\HardDIsk\Windows\sys\config\software
0x3a8 FIleUserName \/\ system root
0x3b0 HiveRootPath \REGISTRY\MACHINE\SOFTWARE
_HHIVE
Signature is 0xbee0bee0
>>> dt("_HHIVE")
'_HHIVE' (748 bytes)
0x0 : Signature ['unsigned long']
0x4 : GetCellRoutine ['pointer', ['void']]
0x8 : ReleaseCellRoutine ['pointer', ['void']]
0xc : Allocate ['pointer', ['void']]
0x10 : Free ['pointer', ['void']]
0x14 : FileSetSize ['pointer', ['void']]
0x18 : FileWrite ['pointer', ['void']]
0x1c : FileRead ['pointer', ['void']]
0x20 : FileFlush ['pointer', ['void']]
0x24 : HiveLoadFailure ['pointer', ['void']]
0x28 : BaseBlock ['pointer', ['_HBASE_BLOCK']]
0x2c : DirtyVector ['_RTL_BITMAP']
0x34 : DirtyCount ['unsigned long']
0x38 : DirtyAlloc ['unsigned long']
0x3c : BaseBlockAlloc ['unsigned long']
0x40 : Cluster ['unsigned long']
0x44 : Flat ['unsigned char']
0x45 : ReadOnly ['unsigned char']
0x46 : DirtyFlag ['unsigned char']
0x48 : HvBinHeadersUse ['unsigned long']
0x4c : HvFreeCellsUse ['unsigned long']
0x50 : HvUsedCellsUse ['unsigned long']
0x54 : CmUsedCellsUse ['unsigned long']
0x58 : HiveFlags ['unsigned long']
0x5c : CurrentLog ['unsigned long']
0x60 : LogSize ['array', 2, ['unsigned long']]
0x68 : RefreshCount ['unsigned long']
0x6c : StorageTypeCount ['unsigned long']
0x70 : Version ['unsigned long']
0x74 : Storage ['array', 2, ['_DUAL']]
Presenter Notes
We care about
0x00 signature
0x28 BaseBlock root key of the registry
0x58 Storage virtual address space for keys
Hives in memory
Are not contagious
Configuration Manager (CM) manages virtual memory for registry keys and values
Ceell indexes and virtual addresses are mapped bu the CM
_HHIVE.Storage gives us full access to registry data in memory from CM
0x74 : Storage ['array', 2, ['_DUAL']]
>>> dt("_DUAL")
'_DUAL' (316 bytes)
0x0 : Length ['unsigned long']
0x4 : Map ['pointer', ['_HMAP_DIRECTORY']]
0x8 : SmallDir ['pointer', ['_HMAP_TABLE']]
0xc : Guard ['unsigned long']
0x10 : FreeDisplay ['array', 24, ['_FREE_DISPLAY']]
0x130 : FreeSummary ['unsigned long']
0x134 : FreeBins ['_LIST_ENTRY']
_HHIVE.Storage.Map goes to structures to obtain the address of a key
Presenter Notes
Finding key in memory
>>> dt("_HMAP_DIRECTORY")
'_HMAP_DIRECTORY' (4096 bytes)
0x0 : Directory ['array', 1024, ['pointer', ['_HMAP_TABLE']]]
>>> dt("_HMAP_TABLE")
'_HMAP_TABLE' (8192 bytes)
0x0 : Table ['array', 512, ['_HMAP_ENTRY']]
>>> dt("_HMAP_ENTRY")
'_HMAP_ENTRY' (16 bytes)
0x0 : BlockAddress ['unsigned long']
0x4 : BinAddress ['unsigned long']
0x8 : CmView ['pointer', ['_CM_VIEW_OF_FILE']]
0xc : MemAlloc ['unsigned long']
Presenter Notes
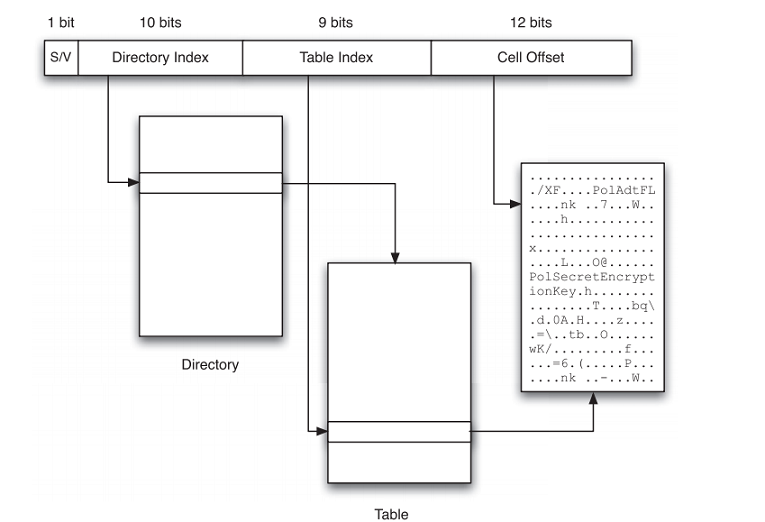
BLockAddress
Once the value of a cell index is known, a key can be found in memory.
Split key into
- 31:31 = Stable/Volatile flag.
- 30:21 = Index into the directory memory
- 20:12 = Table memory
- 11:0 = aoffset within block address where the key data resides.
- Add 4 from block address offset.
Presenter Notes
Presenter Notes
What Registry Keys Matter?
Tons of data in registry.... what matters?
- Auto-start programs
- Hardware
- User account information
- Most recently used lists (MRU)
- System information
- Malware Configurations
Presenter Notes
Hives in memory
There are hives only in memory
- HKEY_LOCAL_MACHINE\Hardware
- HKEY_LOCAL_MACHINE
- HKEY_CURRENT_USER
WinAPI functions cause a flush to disk every 5 seconds
- Malware doesn't use the API and only operates in memory
Presenter Notes
Volatility Hivelist
Scans for CM10 pool tag and prints virtual and physical offsets of hives.
_CMHIVE.HiveList is traversed once a valid _CMHIVE is found
You can supply the offset of a specific hive. Otherwise this module will use the results from hivescan automatically.
-W, --show-unallocated
Skip unallocated objects (e.g. 0xbad0b0b0)
-A START, --start=START
The starting address to begin scanning
-G LENGTH, --length=LENGTH
Length (in bytes) to scan from the starting address
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 hivelist
Volatility Foundation Volatility Framework 2.4
Virtual Physical Name
---------- ---------- ----
0x87c1a248 0x27f67248 \REGISTRY\MACHINE\SYSTEM
0x87c429c8 0x27d519c8 \REGISTRY\MACHINE\HARDWARE
0x8bb5b9c8 0x25e359c8 \SystemRoot\System32\Config\SOFTWARE
0x8bbf0100 0x257a2100 \Device\HarddiskVolume1\Boot\BCD
0x91034008 0x1f326008 \SystemRoot\System32\Config\DEFAULT
0x91113930 0x1e7e4930 \SystemRoot\System32\Config\SECURITY
0x978109c8 0x1ab599c8 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
0x97858008 0x20b92008 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0x978e2008 0x207d0008 \SystemRoot\System32\Config\SAM
0xa0ddc008 0x2d856008 \??\C:\System Volume Information\Syscache.hve
0x8244a008 0x10c58008 \??\C:\Users\Daniel\ntuser.dat
Presenter Notes
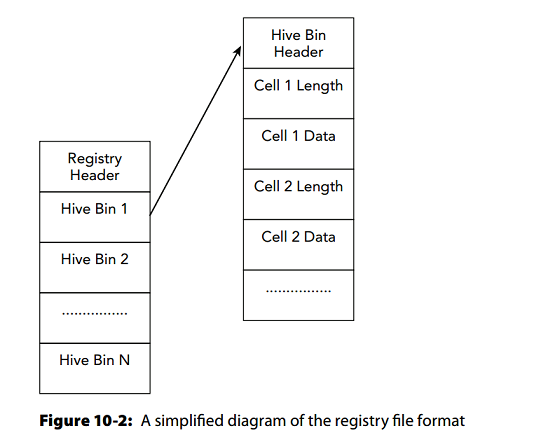
Locating hives
Registry File header is broken into logical hive bins
Each hive bin has a header and is broken into cells
cells contain key and value data
Presenter Notes
Printing Keys and Values
Registry keys are in a tree-like structure with a root key and children keys
Leaf-nodes are subkeys
>>> dt("_CM_KEY_NODE")
'_CM_KEY_NODE' (80 bytes)
0x0 : Signature ['String', {'length': 2}]
0x2 : Flags ['unsigned short']
0x4 : LastWriteTime ['WinTimeStamp', {'is_utc': True}]
0xc : Spare ['unsigned long']
0x10 : Parent ['pointer32', ['_CM_KEY_NODE']]
0x14 : SubKeyCounts ['array', 2, ['unsigned long']]
0x1c : ChildHiveReference ['_CM_KEY_REFERENCE']
0x1c : SubKeyLists ['array', 2, ['unsigned long']]
0x24 : ValueList ['_CHILD_LIST']
0x2c : Security ['unsigned long']
0x30 : Class ['unsigned long']
0x34 : Debug ['BitField', {'end_bit': 32, 'start_bit': 24, 'native_type': 'unsigned long'}]
0x34 : MaxNameLen ['BitField', {'end_bit': 16, 'start_bit': 0, 'native_type': 'unsigned long'}]
0x34 : UserFlags ['BitField', {'end_bit': 20, 'start_bit': 16, 'native_type': 'unsigned long'}]
0x34 : VirtControlFlags ['BitField', {'end_bit': 24, 'start_bit': 20, 'native_type': 'unsigned long'}]
0x38 : MaxClassLen ['unsigned long']
0x3c : MaxValueNameLen ['unsigned long']
0x40 : MaxValueDataLen ['unsigned long']
0x44 : WorkVar ['unsigned long']
0x48 : NameLength ['unsigned short']
0x4a : ClassLength ['unsigned short']
0x4c : Name ['String', {'length': <function <lambda> at 0x984c9cc>}]
Presenter Notes
Printkey
Allows you to print a key’s values and data, the list of subkeys, and last write timestamp
Hivescan
0x87c429c8 0x27d519c8 \REGISTRY\MACHINE\HARDWARE
0x8244a008 0x10c58008 \??\C:\Users\Daniel\ntuser.dat
hivescan -h
-V, --virtual Scan virtual space instead of physical
-W, --show-unallocated
Skip unallocated objects (e.g. 0xbad0b0b0)
-A START, --start=START
The starting address to begin scanning
-G LENGTH, --length=LENGTH
Length (in bytes) to scan from the starting address
-o HIVE_OFFSET, --hive-offset=HIVE_OFFSET
Hive offset (virtual)
-K KEY, --key=KEY Registry Key
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 printkey -o 0x87c429c8
Volatility Foundation Volatility Framework 2.4
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \REGISTRY\MACHINE\HARDWARE
Key name: HARDWARE (S)
Last updated: 2013-10-15 18:45:46 UTC+0000
Subkeys:
(S) ACPI
(S) DESCRIPTION
(S) DEVICEMAP
(V) RESOURCEMAP
Values:
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 printkey -o 0x8244a008
Volatility Foundation Volatility Framework 2.4
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \??\C:\Users\Daniel\ntuser.dat
Key name: CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C} (S)
Last updated: 2013-10-15 18:45:59 UTC+0000
Subkeys:
(S) AppEvents
(S) Console
(S) Control Panel
(S) Environment
(S) EUDC
(S) Identities
(S) Keyboard Layout
(S) Network
(S) Printers
(S) Software
(S) System
(V) Volatile Environment
Values:
Presenter Notes
Malware and printkey
Malware loves run/startup keys
For system startup
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
For user logons
- HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows
- HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
Presenter Notes
Run keys and Volatility
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 printkey -K "Microsoft\Windows\CurrentVersion\Run"
Volatility Foundation Volatility Framework 2.4
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \SystemRoot\System32\Config\SOFTWARE
Key name: Run (S)
Last updated: 2013-10-05 07:33:58 UTC+0000
Subkeys:
Values:
REG_SZ VMware User Process : (S) "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 printkey -K "Software\Microsoft\Windows\CurrentVersion\Run"
Volatility Foundation Volatility Framework 2.4
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
Key name: Run (S)
Last updated: 2009-07-14 04:34:14 UTC+0000
Subkeys:
Values:
REG_EXPAND_SZ Sidebar : (S) %ProgramFiles%\Windows Sidebar\Sidebar.exe /autoRun
----------------------------
Registry: \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
Key name: Run (S)
Last updated: 2009-07-14 04:34:14 UTC+0000
Subkeys:
Values:
REG_EXPAND_SZ Sidebar : (S) %ProgramFiles%\Windows Sidebar\Sidebar.exe /autoRun
----------------------------
Registry: \??\C:\Users\Daniel\ntuser.dat
Key name: Run (S)
Last updated: 2013-10-15 18:46:10 UTC+0000
Subkeys:
Values:
REG_SZ RESTART_STICKY_NOTES : (S) C:\Windows\system32\StikyNot.exe
Presenter Notes
Registry Keys for Services
HKLM/SYSTEM/CurrentControlSet/Services
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 printkey -K currentcontrolset
Volatility Foundation Volatility Framework 2.4
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \REGISTRY\MACHINE\SYSTEM
Key name: CurrentControlSet (V)
Last updated: 2013-10-15 18:45:46 UTC+0000
Subkeys:
Values:
REG_LINK SymbolicLinkValue : (V) \Registry\Machine\System\ControlSet001
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 printkey -K "ControlSet001\services"
Volatility Foundation Volatility Framework 2.4
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \REGISTRY\MACHINE\SYSTEM
Key name: services (S)
Last updated: 2013-10-15 18:47:10 UTC+0000
Subkeys:
(S) .NET CLR Data
(S) .NET CLR Networking
(S) .NET CLR Networking 4.0.0.0
(S) .NET Data Provider for Oracle
(S) .NET Data Provider for SqlServer
(S) .NETFramework
(S) 1394ohci
(S) ACPI
(S) AcpiPmi
(S) adp94xx
(S) adpahci
(S) adpu320
(S) adsi
(S) AeLookupSvc
(S) AFD
(S) agp440
(S) aic78xx
(S) ALG
(S) aliide
(S) amdagp
(S) amdide
(S) AmdK8
(S) AmdPPM
(S) amdsata
(S) amdsbs
(S) amdxata
(S) AppID
(S) AppIDSvc
(S) Appinfo
(S) AppMgmt
(S) arc
(S) arcsas
(S) AsyncMac
(S) atapi
(S) AudioEndpointBuilder
[snip]
Presenter Notes
Out of memory
Can use dumpfiles and extract hives on Pre-W7
hivedump
To recursively list all subkeys in a hive, use the hivedump command and pass it the virtual address to the desired hive.
0x8244a008 0x10c58008 \??\C:\Users\Daniel\ntuser.dat
--output=text Output in this format (format support is module
specific)
--output-file=OUTPUT_FILE
write output in this file
-v, --verbose Verbose information
-g KDBG, --kdbg=KDBG Specify a specific KDBG virtual address
-k KPCR, --kpcr=KPCR Specify a specific KPCR address
-o HIVE_OFFSET, --hive-offset=HIVE_OFFSET
Hive offset (virtual)
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 hivedump -o 0x8244a008
Volatility Foundation Volatility Framework 2.4
Last Written Key
2013-10-15 18:45:59 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents
2013-10-06 16:36:10 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\.Default
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\ActivatingDocument
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\AppGPFault
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\BlockedPopup
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\CCSelect
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\ChangeTheme
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\Close
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\CriticalBatteryAlarm
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\DeviceConnect
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\DeviceDisconnect
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\DeviceFail
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\DisNumbersSound
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\EmptyRecycleBin
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\FaxBeep
2011-03-04 14:34:02 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\FaxError
2011-03-04 14:34:02 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\FaxLineRings
2011-03-04 14:34:02 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\FaxSent
2011-03-04 14:33:06 UTC+0000 \CMI-CreateHive{6A1C4018-979D-4291-A7DC-7AED1C75B67C}\AppEvents\EventLabels\FeedDiscovered
Presenter Notes
NTUser.dat
Userassist keys
Processes the user ran and the time they were ran
Path of program is rot13 encoded
- Caesar cipher where letters shift 13 places
Userassist
Print userassist registry keys and information
-o HIVE_OFFSET, --hive-offset=HIVE_OFFSET
Hive offset (virtual)
-K KEY, --key=KEY Registry Key
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 userassist
Volatility Foundation Volatility Framework 2.4
----------------------------
Registry: \??\C:\Users\Daniel\ntuser.dat
Key name: Count
Last updated: 2013-10-15 18:48:57 UTC+0000
Subkeys:
Values:
REG_BINARY %ProgramFiles%\Debugging Tools for Windows (x86)\windbg.exe :
Count: 1
Focus Count: 9
Time Focused: 0:03:38.391000
Last updated: 2013-10-15 18:14:36 UTC+0000
0x00000000 00 00 00 00 01 00 00 00 09 00 00 00 23 53 03 00 ............#S..
0x00000010 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000020 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000030 00 00 80 bf 00 00 80 bf ff ff ff ff 80 19 b5 67 ...............g
0x00000040 d2 c9 ce 01 00 00 00 00 ........
REG_BINARY C:\Users\Daniel\Desktop\nasm-2.10.09-installer.exe :
Count: 1
Focus Count: 0
Time Focused: 0:00:05.500000
Last updated: 2013-10-06 16:33:02 UTC+0000
0x00000000 00 00 00 00 01 00 00 00 00 00 00 00 88 13 00 00 ................
0x00000010 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000020 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000030 00 00 80 bf 00 00 80 bf ff ff ff ff d0 65 07 ba .............e..
0x00000040 b1 c2 ce 01 00 00 00 00 ........
REG_BINARY %windir%\system32\calc.exe :
Count: 14
Focus Count: 29
Time Focused: 0:05:47.842000
Last updated: 2013-10-15 18:46:12 UTC+0000
0x00000000 00 00 00 00 0e 00 00 00 1d 00 00 00 ce 4c 05 00 .............L..
0x00000010 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000020 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000030 00 00 80 bf 00 00 80 bf ff ff ff ff 00 f1 39 d2 ..............9.
0x00000040 d6 c9 ce 01 00 00 00 00 ........
REG_BINARY %windir%\system32\SnippingTool.exe :
Count: 12
Focus Count: 18
Time Focused: 0:04:22.811000
Last updated: 2013-10-15 18:46:18 UTC+0000
0x00000000 00 00 00 00 0c 00 00 00 12 00 00 00 a7 00 04 00 ................
0x00000010 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000020 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000030 00 00 80 bf 00 00 80 bf ff ff ff ff a0 03 66 d5 ..............f.
0x00000040 d6 c9 ce 01 00 00 00 00 ........
REG_BINARY %windir%\system32\mspaint.exe :
Count: 10
Focus Count: 12
Time Focused: 0:03:40.594000
Last updated: 2013-10-15 18:46:16 UTC+0000
0x00000000 00 00 00 00 0a 00 00 00 0c 00 00 00 be 5b 03 00 .............[..
0x00000010 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000020 00 00 80 bf 00 00 80 bf 00 00 80 bf 00 00 80 bf ................
0x00000030 00 00 80 bf 00 00 80 bf ff ff ff ff 10 f1 72 d4 ..............r.
0x00000040 d6 c9 ce 01 00 00 00 00 ........
Presenter Notes
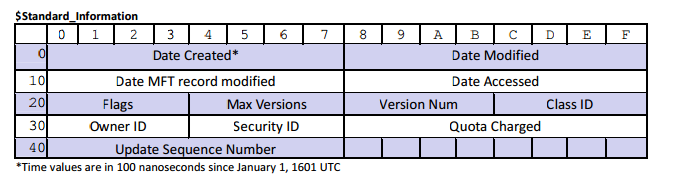
Shimcache
Application Compatibility Database to identify application compatibility issues and their solutions
Keys contain path of executable and $STANDARD_INFORMATION of $MFT
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 shimcache
Volatility Foundation Volatility Framework 2.4
Last Modified Path
------------------------------ ----
2009-07-14 01:14:23 UTC+0000 \??\C:\Windows\system32\makecab.exe
2010-11-20 21:29:13 UTC+0000 \??\C:\Windows\servicing\TrustedInstaller.exe
2010-11-20 21:29:20 UTC+0000 \??\C:\Windows\system32\LogonUI.exe
2009-07-14 01:14:18 UTC+0000 \??\C:\Windows\system32\dllhost.exe
2009-07-14 01:14:21 UTC+0000 \??\C:\Windows\system32\ipconfig.exe
2010-11-20 21:29:12 UTC+0000 \??\C:\Windows\System32\cmd.exe
2012-10-31 22:12:08 UTC+0000 \??\C:\Program Files\VMware\VMware Tools\resume-vm-default.bat
2012-10-31 22:12:08 UTC+0000 \??\C:\Program Files\VMware\VMware Tools\suspend-vm-default.bat
2013-07-21 02:23:42 UTC+0000 \??\C:\Users\Daniel\Desktop\processhacker-2.31-bin\x86\ProcessHacker.exe
2013-02-27 05:05:53 UTC+0000 \??\C:\Windows\system32\consent.exe
2010-11-20 21:29:39 UTC+0000 \??\C:\Windows\System32\mobsync.exe
2010-11-20 21:29:13 UTC+0000 \??\C:\Windows\System32\networkexplorer.dll
2011-05-04 04:28:31 UTC+0000 \??\C:\Windows\system32\SearchFilterHost.exe
2011-05-04 04:28:31 UTC+0000 \??\C:\Windows\system32\SearchProtocolHost.exe
2009-07-14 01:14:18 UTC+0000 \??\C:\Windows\System32\driverquery.exe
2009-07-14 01:14:18 UTC+0000 \??\C:\Windows\System32\dpnsvr.exe
2009-07-13 21:41:43 UTC+0000 \??\C:\Windows\System32\DRWATSON.EXE
2009-07-14 01:14:18 UTC+0000 \??\C:\Windows\system32\DrvInst.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\dvdplay.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\dvdupgrd.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\DWWIN.EXE
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\system32\Dwm.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\dxdiag.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\Dxpserver.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\Eap3Host.exe
2009-07-13 21:40:50 UTC+0000 \??\C:\Windows\System32\edlin.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\efsui.exe
2010-11-20 21:29:21 UTC+0000 \??\C:\Windows\System32\dfrgui.exe
2009-07-14 01:14:19 UTC+0000 \??\C:\Windows\System32\EhStorAuthn.exe
2009-07-14 01:14:17 UTC+0000 \??\C:\Windows\System32\dialer.exe
2009-07-14 01:14:17 UTC+0000 \??\C:\Windows\System32\diantz.exe
2010-11-20 21:29:41 UTC+0000 \??\C:\Windows\System32\audiodev.dll
2010-11-20 21:29:41 UTC+0000 \??\C:\Windows\System32\wpdshext.dll
2006-11-01 18:05:24 UTC+0000 \??\C:\Users\Daniel\Desktop\SysinternalsSuite\efsdump.exe
2006-11-01 18:05:40 UTC+0000 \??\C:\Users\Daniel\Desktop\SysinternalsSuite\hex2dec.exe
2010-04-27 15:04:06 UTC+0000 \??\C:\Users\Daniel\Desktop\SysinternalsSuite\livekd.exe
2006-11-01 18:06:10 UTC+0000 \??\C:\Users\Daniel\Desktop\SysinternalsSuite\ldmdump.exe
2006-11-01 18:06:30 UTC+0000 \??\C:\Users\Daniel\Desktop\SysinternalsSuite\Listdlls.exe
2008-11-18 18:15:14 UTC+0000 \??\C:\Users\Daniel\Desktop\SysinternalsSuite\handle.exe
Presenter Notes
shellbags
Registry keys that track user window viewing preferences
Artifacts
- Windows sizes and preferences
- Icon and folder view settings
- Metadata such as MAC timestamps
- Most Recently Used (MRU) files and file type (zip, directory, installer)
- Files, folders, zip files, and installers that existed at one point on the system (even if deleted)
- Network shares and folders within the shares
- Metadata associated with any of these types that may include timestamps and absolute paths
- Information about TrueCrypt volumes
Presenter Notes
Could do a whole lecture on these...
shellbags
This plugin parses and prints Shellbag information obtained from the registry.
Also parses data using Shellbag data types
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 shellbags
Volatility Foundation Volatility Framework 2.4
Scanning for registries....
Gathering shellbag items and building path tree...
***************************************************************************
Registry: \??\C:\Users\Daniel\ntuser.dat
Key: Software\Microsoft\Windows\Shell\Bags\1\Desktop
Last updated: 2013-10-15 18:45:30 UTC+0000
Value File Name Modified Date Create Date Access Date File Attr Unicode Name
------------------------- -------------- ------------------------------ ------------------------------ ------------------------------ ------------------------- ------------
ItemPos1024x768x96(1) GZIP-1~1.12- 2013-10-06 16:33:54 UTC+0000 2013-10-06 16:33:54 UTC+0000 2013-10-06 16:33:54 UTC+0000 DIR gzip-1.3.12-1-bin
ItemPos1024x768x96(1) PROCES~1.31- 2013-10-15 18:13:28 UTC+0000 2013-10-15 18:13:28 UTC+0000 2013-10-15 18:13:28 UTC+0000 DIR processhacker-2.31-bin
ItemPos1024x768x96(1) SYSINT~1 2011-03-04 14:39:26 UTC+0000 2011-03-04 14:39:26 UTC+0000 2011-03-04 14:39:26 UTC+0000 NI, DIR SysinternalsSuite
ItemPos1024x768x96(1) TRUECR~1 2013-10-06 16:38:34 UTC+0000 2013-10-05 01:33:00 UTC+0000 2013-10-06 16:38:34 UTC+0000 DIR TrueCrypt
ItemPos1024x768x96(1) nasm.lnk 2013-10-06 16:33:06 UTC+0000 2013-10-06 16:33:06 UTC+0000 2013-10-06 16:33:06 UTC+0000 ARC nasm.lnk
ItemPos1024x768x96(1) PROCES~1.ZIP 2013-10-15 18:13:08 UTC+0000 2013-10-15 18:13:18 UTC+0000 2013-10-15 18:13:18 UTC+0000 ARC, NI processhacker-2.31-bin.zip
ItemPos1024x768x96(1) TRUECR~1.ZIP 2013-10-05 01:32:24 UTC+0000 2013-10-05 01:32:30 UTC+0000 2013-10-05 01:32:30 UTC+0000 ARC, NI TrueCrypt 7.1a Source.zip
ItemPos1024x768x96(1) WINSDK~1.EXE 2013-10-06 16:11:04 UTC+0000 2013-10-06 16:11:40 UTC+0000 2013-10-06 16:11:40 UTC+0000 ARC, NI winsdk_web.exe
ItemPos1024x768x96(1) VMWARE~1.LNK 2013-10-15 18:45:08 UTC+0000 2013-10-06 19:16:02 UTC+0000 2013-10-15 18:45:08 UTC+0000 ARC VMware Shared Folders.lnk
***************************************************************************
***************************************************************************
Registry: \??\C:\Users\Daniel\AppData\Local\Microsoft\Windows\UsrClass.dat
Key: Local Settings\Software\Microsoft\Windows\Shell\BagMRU
Last updated: 2013-10-15 18:47:04 UTC+0000
Value Mru Entry Type GUID GUID Description Folder IDs
------- ----- -------------- ---------------------------------------- -------------------- ----------
1 2 Folder Entry 20d04fe0-3aea-1069-a2d8-08002b30309d My Computer EXPLORER, MY_COMPUTER
Value Mru File Name Modified Date Create Date Access Date File Attr Path
------- ----- -------------- ------------------------------ ------------------------------ ------------------------------ ------------------------- ----
0 3 SYSINT~1 2011-03-04 14:39:26 UTC+0000 2011-03-04 14:39:26 UTC+0000 2011-03-04 14:39:26 UTC+0000 NI, DIR SysinternalsSuite
3 6 TrueCrypt 7.1a Source 1970-01-01 00:00:00 UTC+0000 1970-01-01 00:00:00 UTC+0000 1970-01-01 00:00:00 UTC+0000 DIR TrueCrypt 7.1a Source
Value Mru Entry Type GUID GUID Description Folder IDs
------- ----- -------------- ---------------------------------------- -------------------- ----------
2 1 Folder Entry 26ee0668-a00a-44d7-9371-beb064c98683 {Unknown CSIDL} EXPLORER, MY_COMPUTER, RECYCLE_BIN, UKNOWN
Value Mru File Name Modified Date Create Date Access Date File Attr Path
------- ----- -------------- ------------------------------ ------------------------------ ------------------------------ ------------------------- ----
5 7 pkcs 2013-10-06 14:48:04 UTC+0000 2013-10-06 16:32:30 UTC+0000 2013-10-06 16:32:30 UTC+0000 NI, DIR pkcs
4 5 gzip-1.3.12-1-bin 1970-01-01 00:00:00 UTC+0000 1970-01-01 00:00:00 UTC+0000 1970-01-01 00:00:00 UTC+0000 DIR gzip-1.3.12-1-bin
7 0 processhacker-2.31-bin 1970-01-01 00:00:00 UTC+0000 1970-01-01 00:00:00 UTC+0000 1970-01-01 00:00:00 UTC+0000 DIR processhacker-2.31-bin
6 4 TRUECR~1 2013-10-06 16:38:20 UTC+0000 2013-10-05 01:33:00 UTC+0000 2013-10-06 16:38:20 UTC+0000 DIR TrueCrypt
***************************************************************************
***************************************************************************
Registry: \??\C:\Users\Daniel\AppData\Local\Microsoft\Windows\UsrClass.dat
Key: Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1
Last updated: 2013-10-06 19:20:20 UTC+0000
Value Mru Entry Type Path
------- ----- -------------- ----
1 3 Volume Name A:\
0 0 Volume Name C:\
3 1 Volume Name Z:\
2 2 Volume Name D:\
***************************************************************************
***************************************************************************
Registry: \??\C:\Users\Daniel\AppData\Local\Microsoft\Windows\UsrClass.dat
Key: Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4
Last updated: 2013-10-06 18:07:31 UTC+0000
Value Mru File Name Modified Date Create Date Access Date File Attr Path
------- ----- -------------- ------------------------------ ------------------------------ ------------------------------ ------------------------- ----
0 0 bin 2013-10-06 16:33:54 UTC+0000 2013-10-06 16:33:54 UTC+0000 2013-10-06 16:33:54 UTC+0000 DIR gzip-1.3.12-1-bin\bin
***************************************************************************
Presenter Notes
Hashdump
Dumps keys from SYSTEM and SAM hives which contain password hashes (LM and NT hash)
NT hash is on all Windows
- Also called NTLM hash
- v1 uses MD4 hashing algorithm without salting
LM hash is easy to crack and is disabled in Vista+
Stored by Username:RID:LMHash:NTLMHash
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 hashdump
Volatility Foundation Volatility Framework 2.4
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Daniel:1000:aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c:::
Use cracker/website/rainbow table/etc
8846f7eaee8fb117ad06bdd830b7586c NTLM : password
Presenter Notes
RID = Releative Id of the user SID
15+ characters = no LM hashes in memory
Timestomping
Anti-registry forensics technique
Write over Last Update time on a registry key to a ridiculous number
SetRegTime by Joakim Schicht uses NtSetInformationKey to perform this
NTSTATUS NtSetInformationKey(
_In_ HANDLE KeyHandle,
_In_ KEY_SET_INFORMATION_CLASS KeySetInformationClass,
_In_ PVOID KeySetInformation,
_In_ ULONG KeySetInformationLength
);
Presenter Notes
WinAPI
Lots of WinAPI for registry
2 important
LONG WINAPI RegCreateKeyEx(
_In_ HKEY hKey,
_In_ LPCTSTR lpSubKey,
_Reserved_ DWORD Reserved,
_In_opt_ LPTSTR lpClass,
_In_ DWORD dwOptions,
_In_ REGSAM samDesired,
_In_opt_ LPSECURITY_ATTRIBUTES lpSecurityAttributes,
_Out_ PHKEY phkResult,
_Out_opt_ LPDWORD lpdwDisposition
);
and
LONG WINAPI RegSetValueEx(
_In_ HKEY hKey,
_In_opt_ LPCTSTR lpValueName,
_Reserved_ DWORD Reserved,
_In_ DWORD dwType,
_In_ const BYTE *lpData,
_In_ DWORD cbData
);