Networking
Presenter Notes
What
Malware and Networking
Windows API
Microsoft's TCP/IP
Presenter Notes
Sockets and Connections
Sockets
- Endpoints for communications
Clients contain client sockets
- Initiate connections
Servers contain server sockets
- Listen for incoming connections
Presenter Notes
Creating Sockets
Ws2_32.dll
- Main windows networking DLL
- Socket function
Wininet.dll
- High level networking DLL for protocols such as FTP and HTTP.
- Wrappers on Winsock2 functions
Winsock2
- Windows Sockets 2
- Create advanced Internet, intranet, and other network-capable applications to transmit application data across the wire, independent of the network protocol being used.
Presenter Notes
Kernel
- Transport Driver Interface (TDI)
- Used by higher-level components such as Winsock
Presenter Notes
Winsock
Windows Sockets API
Passess
- IP Family (AF_INET = ipv4)
- A type (SOCK_STREAM, SOCK_DGRAM, SOCK_RAW)
- A protocol (IPROTO_TCP, IPPROTO_UDP, IPPROTO_IP, IPPROTO_ICMP)
After a socket is created it must be bound to a port and listened.
- API = bind and listen
Clients call connect.
Presenter Notes
Berkeley Compatible Sockets
Windows uses Berkeley compatible sockets in the Winsock Libraries
| Function | Description |
|----------|--------------------------------------------------------|
| Socket | Create a socket |
| bind | Attach to a socket on a port |
| listen | Listen for incoming connections |
| accept | Open and accept a connection |
| connect | Open a connection to a remote socket that is listening |
| recv | Recieve data from the remote socket |
| send | Send data to remote socket |
Presenter Notes
Establishing a connection
Windows uses the API call WSAStartup before any networking functions can be used
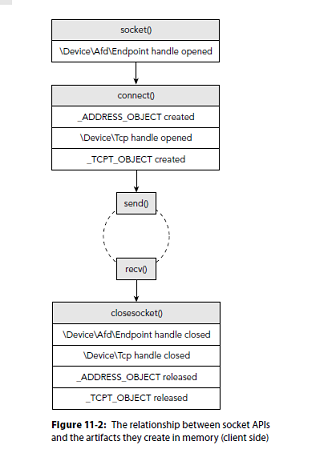
Presenter Notes
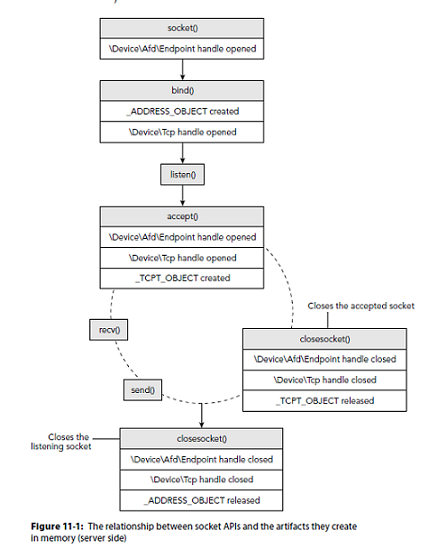
Presenter Notes
What to look for
Rouge listeners
Suspicious connections
Promiscuous network cards
Hidden ports
Browser History
Presenter Notes
Structures
>>> dt("_ADDRESS_OBJECT")
'_ADDRESS_OBJECT' (104 bytes)
0x0 : Next ['pointer', ['_ADDRESS_OBJECT']]
0x2c : LocalIpAddress ['IpAddress']
0x30 : LocalPort ['unsigned be short']
0x32 : Protocol ['unsigned short']
0x148 : Pid ['unsigned long']
0x158 : CreateTime ['WinTimeStamp', {'is_utc': True}]
>>>
>>> dt("_TCPT_OBJECT")
'_TCPT_OBJECT' (32 bytes)
0x0 : Next ['pointer', ['_TCPT_OBJECT']]
0xc : RemoteIpAddress ['IpAddress']
0x10 : LocalIpAddress ['IpAddress']
0x14 : RemotePort ['unsigned be short']
0x16 : LocalPort ['unsigned be short']
0x18 : Pid ['unsigned long']
Both are Undocumented
Presenter Notes
In Memory
Connections are stored in a hash table using Separate Chaining
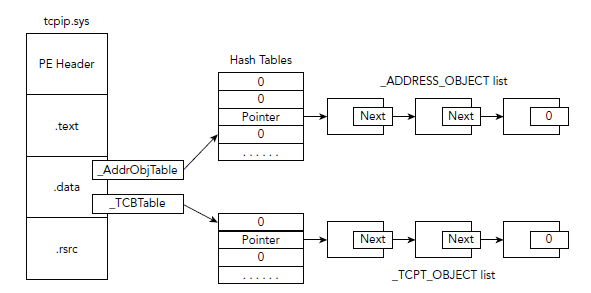
Presenter Notes
Port Numbers
0 -> 1023 = Well-known / system ports
1024 -> 49151 = ephermeral client or server ports and are registered ports by IANA.
49152 -> 65535 = unregistered ports
Presenter Notes
Sockets
Print list of open sockets
Only works on XP and 2003 Server Images
vol.py sockets -f zeus.bin --profile=WinXPSP3x86
Volatility Foundation Volatility Framework 2.4
PID Port Proto Protocol Address Create Time
-------- ------ ------ --------------- --------------- -----------
892 19705 6 TCP 0.0.0.0 2009-02-12 03:38:14
Presenter Notes
Sorted
PID Port Proto Protocol Address Create Time
-------- ------ ------ --------------- --------------- -----------
1064 1276 17 UDP 127.0.0.1 2009-02-12 03:38:12
1064 1275 17 UDP 192.168.128.128 2009-02-12 03:38:12
892 19705 6 TCP 0.0.0.0 2009-02-12 03:38:14
892 35335 6 TCP 0.0.0.0 2009-02-12 03:38:14
892 1277 6 TCP 0.0.0.0 2009-02-12 03:38:15
Presenter Notes
What are they?
python vol.py -f zeus.vmem --profile=WinXPSP3x86 pslist | grep 892
Volatility Foundation Volatility Framework 2.4
Name PID PPID Thds Hnds Sess Start
----------------- ------ ------ ------ -------- ------ ------------------
svchost.exe 892 728 26 294 0 2008-09-18 05:32:58
$ python vol.py -f zeus.vmem --profile=WinXPSP3x86 pslist | grep 1064
Volatility Foundation Volatility Framework 2.4
Name PID PPID Thds Hnds Sess Start
----------------- ------ ------ ------ -------- ------ ------------------
svchost.exe 1064 728 62 1235 0 2008-09-18 05:32:59
Presenter Notes
Connections
View TCP connections active at time of acquisition.
Only works on XP and 2003 Server Images
python vol.py -f Win2003SP2x64.vmem --profile=Win2003SP2x64 connections
Volatile Systems Volatility Framework 2.1_alpha
Offset(V) Local Address Remote Address Pid
------------------ ------------------------- ------------------------- ------
0xfffffadfe6f2e2f0 172.16.237.150:1408 72.246.25.25:80 2136
0xfffffadfe72e8080 172.16.237.150:1369 64.4.11.30:80 2136
0xfffffadfe622d010 172.16.237.150:1403 74.125.229.188:80 2136
0xfffffadfe62e09e0 172.16.237.150:1352 64.4.11.20:80 2136
0xfffffadfe6f2e630 172.16.237.150:1389 209.191.122.70:80 2136
0xfffffadfe5e7a610 172.16.237.150:1419 74.125.229.187:80 2136
0xfffffadfe7321bc0 172.16.237.150:1418 74.125.229.188:80 2136
0xfffffadfe5ea3c90 172.16.237.150:1393 216.115.98.241:80 2136
0xfffffadfe72a3a80 172.16.237.150:1391 209.191.122.70:80 2136
0xfffffadfe5ed8560 172.16.237.150:1402 74.125.229.188:80 2136
Presenter Notes
connscan
Only works on XP and 2003 Server Images
Pool tag scan for _TCPT_OBJECT
python vol.py -f Win2K3SP0x64.vmem --profile=Win2003SP2x64 connscan
Volatile Systems Volatility Framework 2.1_alpha
Offset(P) Local Address Remote Address Pid
---------- ------------------------- ------------------------- ------
0x0ea7a610 172.16.237.150:1419 74.125.229.187:80 2136
0x0eaa3c90 172.16.237.150:1393 216.115.98.241:80 2136
0x0eaa4480 172.16.237.150:1398 216.115.98.241:80 2136
0x0ead8560 172.16.237.150:1402 74.125.229.188:80 2136
0x0ee2d010 172.16.237.150:1403 74.125.229.188:80 2136
0x0eee09e0 172.16.237.150:1352 64.4.11.20:80 2136
0x0f9f83c0 172.16.237.150:1425 98.139.240.23:80 2136
0x0f9fe010 172.16.237.150:1394 216.115.98.241:80 2136
Presenter Notes
sockscan
Pool tag scan for _ADDRESS_OBJECT
XP and 2003 Server Only
[root&windows]#volatility -f Lab2.vmem --profile=WinXPSP2x86 sockscan
Volatility Foundation Volatility Framework 2.4
Offset(P) PID Port Proto Protocol Address Create Time
---------- -------- ------ ------ --------------- --------------- -----------
0x014273f8 1392 1900 17 UDP 192.168.145.135 2015-04-02 19:47:09 UTC+0000
0x01455978 1056 123 17 UDP 127.0.0.1 2015-04-02 18:37:38 UTC+0000
0x0145b478 1056 123 17 UDP 192.168.145.135 2015-04-02 18:37:38 UTC+0000
0x0145e4c8 1392 1900 17 UDP 127.0.0.1 2015-04-02 19:47:09 UTC+0000
0x01481938 828 3389 6 TCP 0.0.0.0 2015-04-02 19:38:07 UTC+0000
0x01f16008 4 137 17 UDP 192.168.145.135 2015-04-07 03:05:41 UTC+0000
0x01f181d8 1052 1355 17 UDP 127.0.0.1 2015-04-06 19:04:12 UTC+0000
0x01f218b8 1076 123 17 UDP 192.168.145.135 2015-04-07 03:05:41 UTC+0000
0x01f33680 1076 123 17 UDP 127.0.0.1 2015-04-07 03:05:41 UTC+0000
0x01f5b6e8 876 3389 6 TCP 0.0.0.0 2015-04-04 00:09:19 UTC+0000
0x01f684f8 1752 1028 6 TCP 127.0.0.1 2015-04-04 00:09:11 UTC+0000
0x01f87bb0 696 0 255 Reserved 0.0.0.0 2015-04-04 00:09:00 UTC+0000
0x01f9b5c0 1332 1309 17 UDP 127.0.0.1 2015-04-06 19:03:47 UTC+0000
0x01fabc18 4 1143 6 TCP 0.0.0.0 2015-04-05 03:05:04 UTC+0000
0x020db008 1372 1900 17 UDP 127.0.0.1 2015-04-07 03:05:41 UTC+0000
0x0214c5f0 696 4500 17 UDP 0.0.0.0 2015-04-04 00:09:00 UTC+0000
0x0214cd80 696 500 17 UDP 0.0.0.0 2015-04-04 00:09:00 UTC+0000
0x021b17b8 4 139 6 TCP 192.168.145.135 2015-04-07 03:05:41 UTC+0000
Presenter Notes
Malicious?
Dump executable to disk, restore imports and analyze!
Yara scan in memory to match malware signatures
If DLL Dlldump it!
Injected shellcode? Dump ir ot Disassemble it in VolShell!
Presenter Notes
API calls to watch
| WinSock | WinINet | COM |
|----------------- |------------------- |------------------- |
| WSAStartup | InternetOpen | URLDownloadToFile |
| getaddrinfo | InternetConnect | CoInitialize |
| socket | InternetOpenURL | CoCreateInstance |
| connect | InternetReadFile | Navigate |
| send | InternetWriteFile | |
| recv | HttpOpenRequest | |
| WSAGetLastError | HTTPQueryInfo | |
| | | |
Presenter Notes
IDA Networking Calls
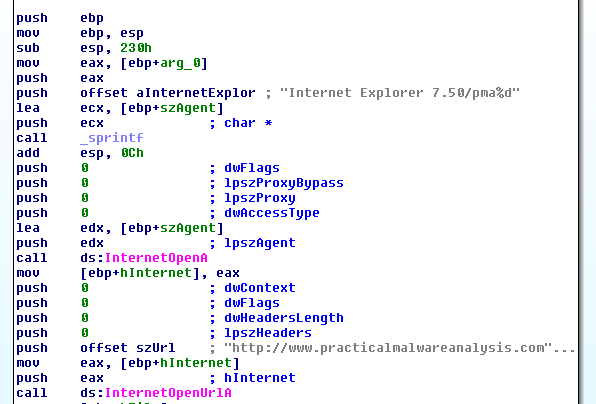
Presenter Notes
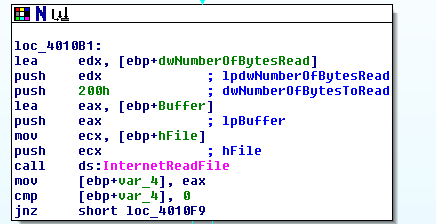
Presenter Notes
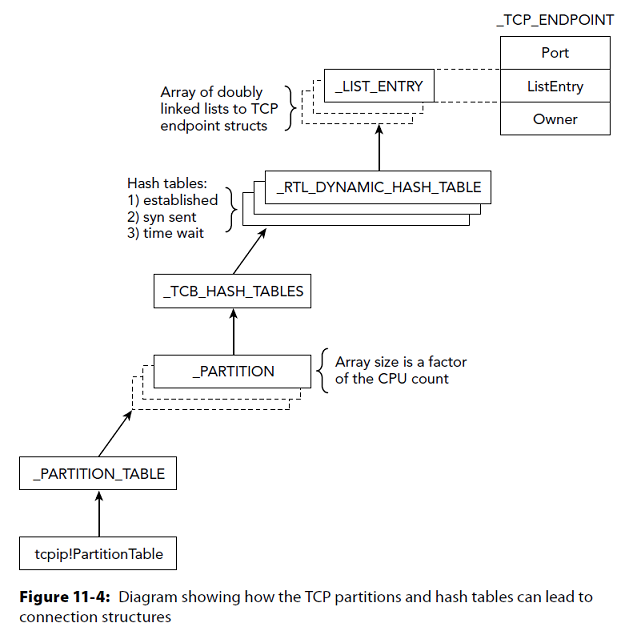
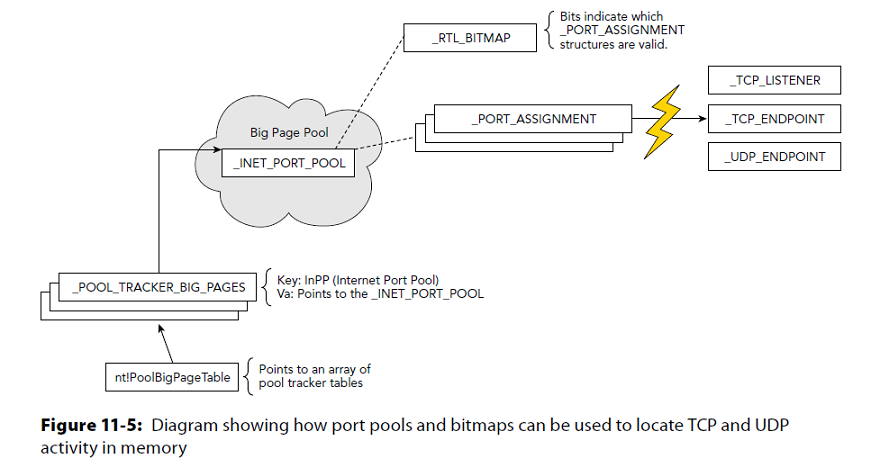
Netscan
Windows Vista + network artifacts using pool-scanning
Scans
- _TCP_ENDPOINT
- _TCP_LISTENER
- _UDP_ENDPOINT
Distinguishes between IPv4 and IPv6
prints
- the local and remote IP
- the local and remote port
- the time when the socket was bound or when the connection was established
- the current TCP state
Presenter Notes
Structures TCP
>>> dt("_TCP_ENDPOINT")
'_TCP_ENDPOINT' (None bytes)
0x0 : CreateTime ['WinTimeStamp', {'is_utc': True, 'value': 0}]
0xc : InetAF ['pointer', ['_INETAF']]
0x10 : AddrInfo ['pointer', ['_ADDRINFO']]
0x14 : ListEntry ['_LIST_ENTRY']
0x34 : State ['Enumeration', {'target': 'long', 'choices': {0: 'CLOSED', 1: 'LISTENING', 2: 'SYN_SENT', 3: 'SYN_RCVD', 4: 'ESTABLISHED', 5: 'FIN_WAIT1', 6: 'FIN_WAIT2', 7: 'CLOSE_WAIT', 8: 'CLOSING', 9: 'LAST_ACK', 12: 'TIME_WAIT', 13: 'DELETE_TCB'}}]
0x38 : LocalPort ['unsigned be short']
0x3a : RemotePort ['unsigned be short']
0x174 : Owner ['pointer', ['_EPROCESS']]
>>> dt("_TCP_LISTENER")
'_TCP_LISTENER' (None bytes)
0x18 : Owner ['pointer', ['_EPROCESS']]
0x20 : CreateTime ['WinTimeStamp', {'is_utc': True}]
0x34 : LocalAddr ['pointer', ['_LOCAL_ADDRESS']]
0x38 : InetAF ['pointer', ['_INETAF']]
0x3e : Port ['unsigned be short']
Presenter Notes
Structures UDP
>>> dt("_UDP_ENDPOINT")
'_UDP_ENDPOINT' (None bytes)
0x14 : InetAF ['pointer', ['_INETAF']]
0x18 : Owner ['pointer', ['_EPROCESS']]
0x30 : CreateTime ['WinTimeStamp', {'is_utc': True}]
0x38 : LocalAddr ['pointer', ['_LOCAL_ADDRESS']]
0x48 : Port ['unsigned be short']
Presenter Notes
Netscan
(-) means results could not be found in memory dump.
Information in structures are pointers to pointers and are not always there if pages are swapped.
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 netscan
Volatility Foundation Volatility Framework 2.4
Offset(P) Proto Local Address Foreign Address State Pid Owner Created
0x3da07008 UDPv4 0.0.0.0:0 *:* 2876 devenv.exe 2013-10-15 18:46:18 UTC+0000
0x3da07008 UDPv6 :::0 *:* 2876 devenv.exe 2013-10-15 18:46:18 UTC+0000
0x3da076c0 UDPv4 0.0.0.0:0 *:* 2876 devenv.exe 2013-10-15 18:46:18 UTC+0000
0x3dad5a18 UDPv4 0.0.0.0:0 *:* 2876 devenv.exe 2013-10-15 18:46:18 UTC+0000
0x3dad5a18 UDPv6 :::0 *:*
0x3ddca628 TCPv4 0.0.0.0:49178 0.0.0.0:0 LISTENING 520 lsass.exe
0x3ddca628 TCPv6 :::49178 :::0 LISTENING 520 lsass.exe
0x3ddcdf60 TCPv4 0.0.0.0:49178 0.0.0.0:0 LISTENING 520 lsass.exe
0x3da2db78 TCPv4 192.168.228.159:49210 63.241.108.124:80 CLOSED -------- --------------
0x3dab8570 TCPv4 192.168.228.159:49203 70.37.57.244:80 CLOSED -------- --------------
0x3dad6008 TCPv4 192.168.228.159:49202 64.4.11.25:80 CLOSED -------- --------------
0x3ef65af8 UDPv4 192.168.228.159:138 *:* 4 System 2013-10-15 18:48:52 UTC+0000
0x3f309200 TCPv4 192.168.228.159:49204 65.55.57.27:80 CLOSED -------- --------------
Presenter Notes
Indicators and Investigation
[root&windows]#whois 64.4.11.25
NetRange: 64.4.0.0 - 64.4.63.255
CIDR: 64.4.0.0/18
NetName: MICROSOFT
[root&windows]#whois 70.37.57.244
NetRange: 70.37.0.0 - 70.37.191.255
CIDR: 70.37.128.0/18, 70.37.0.0/17
NetName: MICROSOFT
Presenter Notes
With Yara
Use yara to discover web related activity in memory
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 yarascan --wide -Y "http"
Rule: r1
Owner: Process taskhost.exe Pid 320
0x772c5eb0 68 00 74 00 74 00 70 00 00 00 00 00 66 00 74 00 h.t.t.p.....f.t.
0x772c5ec0 70 00 00 00 67 00 6f 00 70 00 68 00 65 00 72 00 p...g.o.p.h.e.r.
0x772c5ed0 00 00 00 00 6d 00 61 00 69 00 6c 00 74 00 6f 00 ....m.a.i.l.t.o.
0x772c5ee0 00 00 00 00 6e 00 65 00 77 00 73 00 00 00 00 00 ....n.e.w.s.....
0x772c5ef0 6e 00 6e 00 74 00 70 00 00 00 00 00 74 00 65 00 n.n.t.p.....t.e.
0x772c5f00 6c 00 6e 00 65 00 74 00 00 00 00 00 77 00 61 00 l.n.e.t.....w.a.
0x772c5f10 69 00 73 00 00 00 00 00 6d 00 6b 00 00 00 00 00 i.s.....m.k.....
Find a firewall log for an IP address?
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 yarascan --wide -Y "192.168"
Owner: Process VSSVC.exe Pid 580
0x002d84b8 31 00 39 00 32 00 2e 00 31 00 36 00 38 00 2e 00 1.9.2...1.6.8...
0x002d84c8 32 00 32 00 38 00 2e 00 31 00 35 00 39 00 00 00 2.2.8...1.5.9...
Owner: Process VSSVC.exe Pid 580
0x0029f620 31 00 39 00 32 00 2e 00 31 00 36 00 38 00 2e 00 1.9.2...1.6.8...
0x0029f630 32 00 32 00 38 00 2e 00 31 00 35 00 39 00 00 00 2.2.8...1.5.9...
Presenter Notes
Slim it down
From knowing what processes had network connections, use -p to find only connections that appeared malicious
[root&windows]#volatility -f Win7.bin --profile=Win7SP0x86 yarascan --wide -Y "http" -p 520
Volatility Foundation Volatility Framework 2.4
Rule: r1
Owner: Process lsass.exe Pid 520
0x752bd3a4 68 00 74 00 74 00 70 00 00 00 90 90 6e 00 63 00 h.t.t.p.....n.c.
0x752bd3b4 61 00 6c 00 72 00 70 00 63 00 00 00 6e 00 63 00 a.l.r.p.c...n.c.
0x752bd3c4 61 00 63 00 6e 00 5f 00 6e 00 70 00 00 00 90 90 a.c.n._.n.p.....
0x752bd3d4 6e 00 63 00 61 00 63 00 6e 00 5f 00 69 00 70 00 n.c.a.c.n._.i.p.
0x752bd3e4 5f 00 74 00 63 00 70 00 00 00 90 90 90 90 90 8b _.t.c.p.........
0x752bd3f4 ff 55 8b ec 83 ec 0c 8b 45 08 c1 e0 02 8b 88 74 .U......E......t
0x752bd404 ad 32 75 33 d2 c7 45 f4 0c 00 00 00 c7 45 f8 04 .2u3..E......E..
0x752bd414 00 00 00 89 55 fc 3b ca 0f 84 9d 02 00 00 56 8d ....U.;.......V.
0x752bd424 75 f4 56 52 51 6a 0a ff b0 60 ad 32 75 ff 15 d8 u.VRQj...`.2u...
0x752bd434 90 32 75 5e c9 c2 04 00 90 90 90 90 90 ff 25 e4 .2u^..........%.
0x752bd444 13 2b 75 90 90 90 90 90 6a 64 68 80 d5 2b 75 e8 .+u.....jdh..+u.
0x752bd454 9c 41 ff ff 33 f6 89 75 e0 c6 45 e7 00 c6 45 e6 .A..3..u..E...E.
0x752bd464 00 32 db 89 75 d0 89 75 dc 33 d2 42 89 55 d4 89 .2..u..u.3.B.U..
0x752bd474 75 cc 6a 07 59 33 c0 8d 7d b0 f3 ab 6a 09 59 8d u.j.Y3..}...j.Y.
0x752bd484 7d 8c f3 ab 89 75 fc 52 56 56 ff 15 8c 92 32 75 }....u.RVV....2u
0x752bd494 89 45 d0 3b c6 0f 84 bc 16 00 00 68 85 00 00 00 .E.;.......h....
Presenter Notes
Hiding Information
Hook user mode APIs
- DeviceIoControl
- ZqDeviceIoControlFile
- GetTcpTable
Install Kernel Drive to hook tcpip.sys driver
Create a driver, NDIS, to operate lower than Winsock2 and bypass socket and connection object creation
- The Network Driver Interface Specification (NDIS) library abstracts the network hardware from network drivers.
Pooltag scanning eliminates these. Also finding IP packets or eth frames in memory dump.
*Note: DKOM does not work on TCP/IP structures, but you can overwrite pool tags. *
Presenter Notes
Raw Sockets
Admin processes can enable raw sockets through Winsock2.
Enable programs to access transport layer data and forge/spoof packets.
Can use raw sockets in promiscuous mode and capture information going over wire.
- Passes and receives all traffic. Packet sniffing.
Two types:
- IP header and recognized by Winsock service provider.
- Any protocol. Make your own!
SOCKET s = socket(AF_INET, SOCK_RAW, IPPROTO_IP);
Presenter Notes
Detecting Raw Sockets
Live: Promiscdetect
Volatility: Sockets or Handles
Look for oddly named protocols
$ python vol.py sockets -f ursniff.vmem --profile=WinXPSP3x86
Volatility Foundation Volatility Framework 2.4
PID Port Proto Protocol Address Create Time
-------- ------ ------ --------------- --------------- -----------
1052 123 17 UDP 172.16.99.130 2009-11-18 01:23:24
716 500 17 UDP 0.0.0.0 2009-11-18 01:23:20
1824 0 0 HOPOPT 172.16.99.130 2010-01-07 20:29:10
[...]
$ python vol.py files -p 1824 -f ursniff.vmem --profile=WinXPSP3x86
Volatility Foundation Volatility Framework 2.4
Offset(V) Pid Handle Access Type Details
---------- ------ ---------- ---------- ---------------- -------
0x818f9f90 1824 0xa0 0x1f01ff File \Device\Afd\Endpoint
0x814d4b70 1824 0xa8 0x1f01ff File \Device\RawIp\0
0x8145bf90 1824 0xd0 0x1f01ff File \Device\Afd\Endpoint
0x8155cf90 1824 0xd4 0x1f01ff File \Device\Tcp
[...]
Presenter Notes
Windows Vista+
Presenter Notes
Presenter Notes
Internet History
Chrome and Firefox use a SQLite database.
- That database is opened and read when a browser loads
Internet Explorer
- Uses .dat files
- Index .dat is history
Presenter Notes
Obtaining History
- Find internet process
- Locate signature of database or file
- ????
- Profit
[root&windows]#volatility -f Lab2.vmem --profile=WinXPSP2x86 pslist | grep iexplore
Volatility Foundation Volatility Framework 2.4
0x81d79da0 iexplore.exe 1052 1756 12 484 0 0 2015-04-06 19:03:42 UTC+0000
0x81fa8ad0 iexplore.exe 1332 1052 20 797 0 0 2015-04-06 19:03:46 UTC+0000
Presenter Notes
Cont
[root&windows]#volatility -f Lab2.vmem --profile=WinXPSP2x86 yarascan -p 1052,1332 -Y "/(URL |REDR|LEAK)/"
Owner: Process iexplore.exe Pid 1332
0x01115600 55 52 4c 20 02 00 00 00 f0 9a ab 8d 76 70 d0 01 URL.........vp..
0x01115610 f0 a2 81 76 a0 70 d0 01 a2 46 18 9c 00 00 00 00 ...v.p...F......
0x01115620 00 00 00 00 00 00 00 00 00 00 00 00 80 51 01 00 .............Q..
0x01115630 60 00 00 00 68 00 00 00 fe 00 10 10 00 00 00 00 `...h...........
0x01115640 04 00 20 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x01115650 86 46 18 9c 01 00 00 00 00 00 00 00 00 00 00 00 .F..............
0x01115660 00 00 00 00 ef be ad de 3a 32 30 31 35 30 34 30 ........:2015040
0x01115670 36 32 30 31 35 30 34 30 37 3a 20 41 64 6d 69 6e 620150407:.Admin
0x01115680 40 68 74 74 70 3a 2f 2f 77 77 77 2e 68 61 6e 64 @http://www.hand
0x01115690 67 72 65 70 2e 73 65 2f 72 65 70 6f 73 69 74 6f grep.se/reposito
0x011156a0 72 79 2f 73 6f 75 72 63 65 73 2f 52 6f 6f 74 6b ry/sources/Rootk
0x011156b0 69 74 73 2f 64 72 69 76 65 72 5f 6c 6f 61 64 65 its/driver_loade
0x011156c0 72 2e 63 00 ef be ad de ef be ad de ef be ad de r.c.............
Rule: r1
Owner: Process iexplore.exe Pid 1052
0x00b08b80 55 52 4c 20 02 00 00 00 30 39 6d cd a0 70 d0 01 URL.....09m..p..
0x00b08b90 30 39 6d cd a0 70 d0 01 a2 46 83 9b 00 00 00 00 09m..p...F......
0x00b08ba0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00b08bb0 60 00 00 00 68 00 00 00 fe 00 10 10 00 00 00 00 `...h...........
0x00b08bc0 01 00 20 00 9c 00 00 00 14 00 00 00 00 00 00 00 ................
0x00b08bd0 86 46 67 9c 01 00 00 00 00 00 00 00 00 00 00 00 .Fg.............
0x00b08be0 00 00 00 00 ef be ad de 56 69 73 69 74 65 64 3a ........Visited:
0x00b08bf0 20 41 64 6d 69 6e 40 68 74 74 70 3a 2f 2f 77 77 .Admin@http://ww
0x00b08c00 77 2e 6f 73 72 6f 6e 6c 69 6e 65 2e 63 6f 6d 2f w.osronline.com/
0x00b08c10 6c 6f 67 69 6e 2e 63 66 6d 00 ad de 10 00 02 00 login.cfm.......
Rule: r1
Owner: Process iexplore.exe Pid 1052
0x00b06700 55 52 4c 20 02 00 00 00 e0 2a 22 d1 a0 70 d0 01 URL......*"..p..
0x00b06710 e0 2a 22 d1 a0 70 d0 01 a2 46 86 9b 00 00 00 00 .*"..p...F......
0x00b06720 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00b06730 60 00 00 00 68 00 00 00 fe 00 10 10 00 00 00 00 `...h...........
0x00b06740 01 00 20 00 98 00 00 00 14 00 00 00 00 00 00 00 ................
0x00b06750 86 46 6a 9c 01 00 00 00 00 00 00 00 00 00 00 00 .Fj.............
0x00b06760 00 00 00 00 ef be ad de 56 69 73 69 74 65 64 3a ........Visited:
0x00b06770 20 41 64 6d 69 6e 40 66 69 6c 65 3a 2f 2f 2f 43 .Admin@file:///C
0x00b06780 3a 2f 62 69 6e 2f 6f 73 72 6c 6f 61 64 65 72 76 :/bin/osrloaderv
0x00b06790 33 30 2e 7a 69 70 00 de 10 00 02 00 00 00 00 10 30.zip..........
Rule: r1
Owner: Process iexplore.exe Pid 1052
0x00b01c80 55 52 4c 20 02 00 00 00 b0 57 91 27 8c 6d d0 01 URL......W.'.m..
0x00b01c90 b0 57 91 27 8c 6d d0 01 9c 46 bb ab 00 00 00 00 .W.'.m...F......
0x00b01ca0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00b01cb0 60 00 00 00 68 00 00 00 fe 00 10 10 00 00 00 00 `...h...........
0x00b01cc0 01 00 20 00 90 00 00 00 14 00 00 00 00 00 00 00 ................
0x00b01cd0 82 46 bb ab 01 00 00 00 00 00 00 00 00 00 00 00 .F..............
0x00b01ce0 00 00 00 00 ef be ad de 56 69 73 69 74 65 64 3a ........Visited:
0x00b01cf0 20 41 64 6d 69 6e 40 66 69 6c 65 3a 2f 2f 2f 43 .Admin@file:///C
0x00b01d00 3a 2f 62 69 6e 2f 67 65 74 70 69 70 2e 70 79 00 :/bin/getpip.py.
Owner: Process iexplore.exe Pid 1052
0x00b00d00 55 52 4c 20 04 00 00 00 10 18 6c 73 8b 6d d0 01 URL.......ls.m..
0x00b00d10 00 62 6e 73 8b 6d d0 01 9c 46 19 ab 00 00 00 00 .bns.m...F......
0x00b00d20 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
0x00b00d30 60 00 00 00 68 00 00 00 fe 00 10 10 00 00 00 00 `...h...........
0x00b00d40 01 00 20 00 cc 00 00 00 bc 00 00 00 00 00 00 00 ................
0x00b00d50 82 46 19 ab 1b 00 00 00 00 00 00 00 00 00 00 00 .F..............
0x00b00d60 00 00 00 00 ef be ad de 56 69 73 69 74 65 64 3a ........Visited:
0x00b00d70 20 41 64 6d 69 6e 40 68 74 74 70 73 3a 2f 2f 69 .Admin@https://i
0x00b00d80 73 63 2e 73 61 6e 73 2e 65 64 75 2f 2f 64 69 61 sc.sans.edu//dia
0x00b00d90 72 79 2f 57 69 6e 70 6d 65 6d 2b 2d 2b 4d 69 6c ry/Winpmem+-+Mil
0x00b00da0 64 2b 6d 61 6e 6e 65 72 65 64 2b 6d 65 6d 6f 72 d+mannered+memor
0x00b00db0 79 2b 61 71 75 69 73 69 74 69 6f 6e 2b 74 6f 6f y+aquisition+too
0x00b00dc0 6c 3f 25 33 66 2f 31 37 30 35 34 00 10 00 02 00 l?%3f/17054.....
0x00b00dd0 00 00 00 00 00 00 00 00 00 00 00 00 a8 00 10 1f ................
0x00b00de0 49 00 6e 00 66 00 6f 00 53 00 65 00 63 00 20 00 I.n.f.o.S.e.c...
0x00b00df0 48 00 61 00 6e 00 64 00 6c 00 65 00 72 00 73 00 H.a.n.d.l.e.r.s.
Presenter Notes
SO what?
We know pip was at least downloaded
We know OSRLOADER was downloaded
- Remember lab 2?
We know winpmem was accessed from the web
Presenter Notes
IEHistory
Reconstruct Internet Explorer cache / history
Output IE history in csv or text
-o OFFSET, --offset=OFFSET
EPROCESS offset (in hex) in the physical address space
-p PID, --pid=PID Operate on these Process IDs (comma-separated)
-n NAME, --name=NAME Operate on these process names (regex)
-L, --leak Find LEAK records (deleted)
-R, --redr Find REDR records (redirected)
[root&windows]#volatility -f Lab2.vmem --profile=WinXPSP2x86 iehistory -p 1052,1332
Volatility Foundation Volatility Framework 2.4
**************************************************
Process: 1052 iexplore.exe
Cache type "URL " at 0xae5000
Record length: 0x100
Location: Cookie:[email protected]/
Last modified: 2015-04-02 19:50:50 UTC+0000
Last accessed: 2015-04-06 19:34:03 UTC+0000
File Offset: 0x100, Data Offset: 0x84, Data Length: 0x0
File: UAPOKXN1.txt
**************************************************
Process: 1332 iexplore.exe
Cache type "URL " at 0x1075400
Record length: 0x100
Location: DOMStore:http://pip.pypa.io/
Last modified: 1970-01-01 00:00:00 UTC+0000
Last accessed: 2015-04-02 21:28:24 UTC+0000
File Offset: 0x100, Data Offset: 0x88, Data Length: 0x0
File: pip.pypa[1].xml
**************************************************
Presenter Notes
Chrome and Firefox?
Brute force!
Use regex and yara!
Websites: "/[a-zA-Z0-9-.]+.(com|org|net|mil|edu|biz|name|info)/"
Mail: ((mailto\:|(news|(ht|f)tp(s?))\://){1}\S+)
Http: ^http\://[a-zA-Z0-9-.]+.[a-zA-Z]{2,3}(/\S*)?$
Presenter Notes
DNS Cache
Svchost.exe runs DNS resolver
- Information stored in heap
system32\drivers\etc\hosts
- Find using filescan
- Dump using dumpfiles
- read
Presenter Notes
Hosts
[root&windows]#volatility -f Lab2.vmem --profile=WinXPSP2x86 filescan | grep hosts
Volatility Foundation Volatility Framework 2.4
0x0000000002089028 1 0 R--rw- \Device\HarddiskVolume1\WINDOWS\system32\drivers\etc\hosts
[root&windows]#mkdir hosts
/bin/mkdir: created directory `hosts'
[root&windows]#volatility -f Lab2.vmem --profile=WinXPSP2x86 dumpfiles -Q 0x0000000002089028 -D hosts/ --name
Volatility Foundation Volatility Framework 2.4
DataSectionObject 0x02089028 None \Device\HarddiskVolume1\WINDOWS\system32\drivers\etc\hosts
[root&windows]#cat hosts/file.None.0x8221fb30.hosts.dat
127.0.0.1 localhost